Class 3 – April 6, 2012 IT Security. IT Security Threats Three types of Security Threats...
-
Upload
marjorie-goodwin -
Category
Documents
-
view
228 -
download
0
Transcript of Class 3 – April 6, 2012 IT Security. IT Security Threats Three types of Security Threats...
IT Security ThreatsThree types of Security Threats (External, Network,
Internal)External- Intrusion Threats
Hacking: Unauthorized access and use of sensitive information Compromising National security data Compromising Personnel data, e.g SSN, Credit cards Compromising Personal data
Cyber crimes ID thefts: on the rise
Identity theft – estimated 10 million people with $50 billion in losses annually according to FTC estimates.
Carding Forums: Criminal websites dedicated to the sale of stolen personal and financial information
IT Security ThreatsThree types of Security Threats (continued)
Network- Technological Threats Network threats (Technological)
System vulnerabilities/ compromises: Security threats due to the software and hardware
itself (some systems can be easily hacked or broken into)
Software is particularly vulnerable. New exploits are found as quickly as existing exploits are patched. Unpatched computers represent an army of drones for use by criminal enterprises.
Malicious software Viruses: Programs that attach to files, enabling
them to spread from one computer to another; can damage hardware, software or files.
Worms: Self-propagating viruses
IT Security ThreatsThree types of Security Threats (continued)
Malicious Software (continued) Botnets – thousands of computers all under the
control of a single hacker or enterprise, used to launch distributed denial of service attacks, flood the network with spam, or store criminal information such as child pornography or stolen information. Once in place, can run autonomously and automatically, requiring little input from “owners.”
Spyware: Programs that are installed without user’s knowledge, and can potentially monitor activities or steal sensitive information
Phishing: Legitimate looking emails that tricks user into providing sensitive information
IT Security ThreatsInternet PiracyOnline software scams that could potentially be
a security threat [see: http://www.bsa.org/files/Internet_Piracy_Report.pdf]
Wireless insecurities Wireless is more prone to security threats than
wired connections Open wireless communities (e.g. Wi-FI hotspots in
public places that do not require a password) are particularly vulnerable
IT Security ThreatsInternal organizational threats
Employee security—who is to guard the guard?Lax management – governments are extensive
data repositories; lax management could compromise the data
Problems of security threatsCorruption of InformationDisclosure of Information to unauthorized
partiesTheft of ServiceDenial-of-service to legitimate users
Containing Security ThreatsLegislative Actions
Computer Security Act (1987) –security guidelines and standards for government computers Gave NIST (National Institute of Standards and
Technology) the mission of developing security standards and guidelines for federal computer systems.
Government Information Security Reform Act (GISRA – 2000) –complemented CSA Complemented CSA. Required agencies to
implement agency-wide information security programs, annual agency program reviews, and annual independent evaluations of security practices by the Inspector General. Oversight by OMB which ultimately reports to Congress.
Containing Security ThreatsLegislative Actions (continued)
Homeland Security Act (HSA – 2002): CIO authority for overseeing coordination and consolidation of data
Federal Information Security Management Act of 2002 (FISMA) Superseded CSA and made most provisions of
GISRA permanent. Strengthened training, evaluation and reporting requirements.
Containing Security ThreatsTotal Information Awareness Project
Virtual database with instant access to information on individuals phone call records, email transcripts, Web search histories, financial records, store purchases, health prescriptions, medical records, educational records, travel history, and transactions involving passports and driver’s licenses. Renamed “Terrorism Information Awareness” project to make it more politically palatable. Attacks came from all sides, both liberal and conservative (civil liberties and bad for business). BUT versions of this already exist, though not as all inclusive – see Accurint and ChoicePoint, for example.
Containing Security ThreatsUpdate software
Install the latest software patches Install antivirus software with frequent updates
Attack halting Stops the attack, whether it is a program or a hacker
Attack blockingCloses the loop-hole through which the attacker gained
access Attack alerting
Either pop-up to an online admin, or email or SMS to a remote admin
Containing Security ThreatsInformation collecting
On what is done by the attack to the network, and from where the attack came - helps gather forensic evidence should a prosecution become necessary or possible
Full reporting Learn from mistakes; prevent future problems
Intrusion Detection SystemsFirewalls
Containing Security ThreatsAccess limitations
Super Power passwordsCAPTCHAs (Completely Automated Turing Test To Tell
Computers and Humans Apart)Multi level access control
Discretionary access control (DAC) Restricted access to objects based on identity of user or
group. Implemented using access control lists to identify which users can access the object and what their rights are.
Mandatory access control (MAC) Restricted access based on sensitivity of information and
authorization of user to access info with that level of sensitivity (top secret, etc.). Administrator controls access by specifying which security labels subject can use.
Containing Security ThreatsRole based access control
Access based on user role within organization. User given no more access or authority than needed to do their job. Concept of “least privilege.”
Task based access controlRather than by role, user given access to
multiple tasks required to perform job. Tasks relate to work responsibility of specific user.
Containing Security ThreatsFail-safe features
Encryption of data to authenticate identity of individuals attempting to access the governmental computer systems
Public Key Infrastructure (PKI) User gets digital certificate from certificate authority
Certificate of authority requires verification of user’s credentials before issuing a digital certificate. Ex. Verisign, Thawte, Digicert, Network Solutions, Smartcom, Trustwave
Certificate creates a public key for the user Certificate authority stores public key in a public registry
Certificate also issues matching private key Private key is stored on user’s computer or on a smart card.
When data is encrypted with your private key, only your public key can decrypt, and vice versa. Sender encrypts the data using the RECEIVER’s public key. Receiver can then decrypt with his or her private key.
User can employ the private key to send encrypted messages Another user can decrypt messages by using the public key Good tutorial on the use of PKI
http://gdp.globus.org/gt4-tutorial/multiplehtml/ch09s03.html
Containing Security ThreatsVPN tunneling through secure channels
VPN = Virtual Private Networking – uses public Internet, but data is encapsulated and encrypted to prevent its interception and use by those not authorized to view the data. Protocols protect, secure, and authenticate data between peer devices.
Federal ID Cards for federal employees and contractors (Smartcards) Smart cards contain verified identifying information
such as a PIN and biometric fingerprint data on a microchip. Includes anti-counterfeit protection.
Real ID Act (2005) – establishes minimum requirements for state issued ID cards and driver’s licenses
Containing Security ThreatsAgency-Level Security Policies
Security governance and reporting Complete inventories of IT assets; listings of critical
infrastructure and mission-critical systems; strong incident identification and reporting procedures; oversight over contractors; strong reporting of security problems.
Physical Security Systems With all the concentration on hackers and the like . . .
Don’t forget to physically secure the system!Security Checks and Clearances
“Hacking out” rather than in. Employees can be a problem, sending information out of the network from their authorized devices within the firewall.
Biometrics Becoming more widely used, still not perfected and
generally not sufficient on its own.
Containing Security ThreatsAgency-Level Security Policies (continued)
Configuration Management Automatic maintenance of networked computers,
enforcing authorized configurations on the user and automating updates and patches.
Secure System Design Planning for breaches; secure and redundant data
backups.Red Teams – teams of experts
Hired to break into the system to determine where vulnerability lies.
Honey Pots – proactive security strategies Intentionally weak devices placed on the network to log
and monitor access attempts. No reasons for any employee to attempt access, so all attempts are suspect.
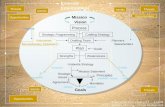
Components of a Comprehensive Security PolicyRisk Management Structure
Formal, highly placed, organizational structure for security planning. Top management representation and support with its own budget. Team performs periodic risk assessments to set security goals.
Data Stewardship Inventory of systems and their related databases with
stewardship given to specific agency personnel tasked with implementing security and privacy policies for their assigned assets.
Risk TrackingDevelop security indicators and measurement
procedures to track all forms of risk. Server logs and monitoring software useful for this purpose.
Components of a Comprehensive Security PolicyRisk Notification
Disseminate information quickly to foster employee awareness and commitment to security.
AuthenticationProcedures to verify the identity of those with whom the
agency shares information. Different access types for different users.
EncryptionProcedures for secure transfer of information
appropriate to assessed risk level.Data Security
Plans for protecting information from external electronic access or physical theft. Also should be protected from insider abuse through security checks and clearances.
Components of a Comprehensive Security PolicyData Sharing
Decisions on how data requests from other agencies and the public will be handled. Should support Freedom of Information Act requests while protecting Personally Identifiable Information and intellectual property.
Data DisposalHow and when to dispose of records.
Security TrainingSecurity procedure training for new employees; security
awareness training for all employees; technical security training for its IT staff.
Incident ResponseAttack recognition – what is the correct first
response?Should the attack be stopped immediately?Call law enforcement?Notify upper management? Who?Even if you are able to stop the attack
immediately, you may not want to do so until you understand the attack fully and identify the intended target and goal of the attack. This may allow the identification of compromised data that might otherwise go unnoticed and the collection of forensic evidence that might lead to prosecution.
Incident ResponseThe role of the Computer Security Incident Response
Team (CSIRT)Organized and tailored to the environment in which it
will operateFramework:
Mission statement: high level goals, objectives and priorities understand if they are using the correct priorities to
ensure they respond to the most important activity correct any inappropriate expectations of those they
interact with understand how and whether it is appropriate for them to
react to a given situation revise their policies and procedures to meet the needs of
the situation determine if the range and nature of the services they
offer should be modified
Incident ResponseThe role of the Computer Security Incident Response
Team (CSIRT)Constituency: who is served and what is the
relationship? Full authority to act for constituency Shared authority – can influence but cannot dictate
decisions No authority – advisors or advocates
Place within the organizational structure and within risk management function Overlaps with security team, but must be part of the
business process, too, since it should establish operational guidelines.
Relationship to others within the organization and without Must be in a position where it can coordinate activities
among groups.CSIRTS are both reactive and proactive in security.