Secure Boot from Encrypted Firmware on EPCS/EPCQ for the...
Transcript of Secure Boot from Encrypted Firmware on EPCS/EPCQ for the...

Secure Boot from Encrypted Firmware on EPCS/EPCQ for the Nios II ecosystemA short Lab for the BeMicro CVA9 board that can be readily adapted for use with any COTS development board
Introduction
Synaptic Labs enables developers to implement a Secure Boot Process from EPCS/Q flash for Nios II and ARM Cortex cores within the Altera Quartus Prime Development Environment. S/Labs offers two types of ECPS/Q secure boot solutions: (a) Boot from cryptographically encrypted firmware; and (b) Boot from cryptographically authenticated and encrypted firmware. This short lab will walk you through the process of booting from cryptographically encrypted firmware stored on EPCQ flash on the BeMicro CVA9 Board. Additional in-depth documentation and tutorials for the secure boot process are available from S/Labs.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �1
An easy to implement solution for encrypting the code and data located in EPCS/Q flash memory.
Additional Resources: ~200 ALM + 1 M10K
S/Labs offers additional IP to increase clock speeds, reduce resource usage and greatly
improve software performance when executing code from off-chip flash
Contact S/Labs for more info: [email protected]
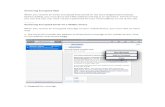
Configure an existing
design to boot from EPCS/Q
Add S/Labs'Security IP in Qsys
to automatically encrypt firmware
Program the EPCS/Q
with encryptedfirmware
Boot from the encrypted firmware
that is stored on EPCS/Q

Prerequisites
• A Windows/Linux PC with two USB ports.
• Altera Quartus Prime with NIOS II EDS installed.
• You must have basic experience with Quartus Prime and Qsys
• This guide was completed with v16.0 of the software but should work with later versions of the Altera Quartus Prime development environment.
• The Arrow BeMicro CVA9 development board (CVA9 board):
• This lab can be trivially adapted by the reader to work with any Altera development board with EPCS/Q support. To do this, please start the project with the vendor’s EPCS/ECPQ enabled Golden Hardware Reference Design (GHRD) project for your development board.
• Installed S/Labs IP:
• Please email Synaptic Labs on [email protected] to request a FREE time-limited, trial license of S/Labs' Secured Off-chip Flash IP. • Please include a copy of your Network Interface Card (NIC) ID in that email. In Quartus Prime, in
the menu bar, click on Tools, then License Setup. The value of the NIC ID can be then located in the bottom half of the License Setup panel of the Options window.
• If approved, you will receive a copy of the encrypted IP tethered to your NIC ID by email. You will also receive an installation guide.
• Please complete the steps described in that installation guide for this IP before proceeding to execute this short lab.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �2

Disclaimer
THIS SOFTWARE, SOURCE CODE AND ASSOCIATED MATERIALS INCLUDING BUT NOT LIMITED TO TUTORIALS, GUIDES AND COMMENTARY PROVIDED WITH THIS EXERCISE ARE ONLY DESIGNED FOR REFERENCE PURPOSES TO GIVE AN EXAMPLE TO LICENSEE FOR THEIR OWN NECESSARY DEVELOPMENT OF THEIR OWN SOFTWARE AND/OR APPLICATION. IT IS NOT DESIGNED FOR ANY SPECIAL PURPOSE, SERIAL PRODUCTION OR USE IN MEDICAL, MILITARY, AIR CRAFT, AVIATION, SPACE OF LIFE SUPPORT EQUIPMENT.
TO THE EXTENT PERMITTED BY LAW, THE EXERCISE SOFTWARE AND/OR SOURCE CODE AND/OR AND ASSOCIATED MATERIALS IS PROVIDED “AS IS” WITHOUT WARRANTY OF ANY KIND AND ONLY FOR REFERENCE PURPOSES.
SYNAPTIC LABORATORIES LTD. MAKES NO WARRANTIES, EITHER EXPRESS OR IMPLIED, WITH RESPECT TO THE LICENSED SOFTWARE AND/OR SOURCE CODE AND/OR ASSOCIATED MATERIALS, CONFIDENTIAL INFORMATION AND DOCUMENTATION PROVIDED HEREUNDER.
SYNAPTIC LABORATORIES LTD. SPECIFICALLY DISCLAIMS THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE AND ANY WARRANTY AGAINST INFRINGEMENT OF ANY INTELLECTUAL PROPERTY RIGHT OF ANY THIRD PARTY WITH REGARD TO THE SOFTWARE, DOCUMENTATION (SCHEMATICS ETC.), SOURCE CODE AND ASSOCIATED MATERIALS, CONFIDENTIAL INFORMATION AND DOCUMENTATION.
ANY USE, COMPILATION AND TESTING OF THE SOFTWARE AND/OR SOURCE CODE IS AT LICENSEE`S OWN RISK AND LICENSEE IS OBLIGED TO CONDUCT EXTENSIVE TESTS TO AVOID ANY ERRORS AND FAILURE IN THE COMPILED SOURCE CODE, DOCUMENTATION (SCHEMATICS ETC.) AND THE HEREFROM GENERATED SOFTWARE OF LICENSEE.
EXCEPT FOR WILFULL INTENT SYNAPTIC LABORATORIES LTD. SHALL IN NO EVENT BE ENTITLED TO OR LIABLE FOR ANY INDIRECT, SPECIAL, INCIDENTAL OR CONSEQUENTIAL DAMAGES OF ANY KIND OR NATURE, INCLUDING, WITHOUT LIMITATION, BUSINESS INTERRUPTION COSTS, LOSS OF PROFIT OR REVENUE, LOSS OF DATA, PROMOTIONAL OR MANUFACTURING EXPENSES, OVERHEAD, COSTS OR EXPENSES ASSOCIATED WITH WARRANTY OR INTELLECTUAL PROPERTY INFRINGEMENT CLAIMS, INJURY TO REPUTATION OR LOSS OF CUSTOMERS.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �3

Table of Contents
Secure Boot from Encrypted Firmware on EPCS/EPCQ for the Nios II ecosystem 1
Introduction 1
Stage 1.a: Configure an existing design to boot from EPCS/Q 5
Stage 1.b: Setup and compile the software in Eclipse 6
Stage 1.c: Convert Programming Files 7
Stage 1.d: Program the EPCQ Flash device 8
Stage 1.e: Program the Cyclone V FPGA device 8
Stage 2.a:Add S'Labs Inline Memory Encryptor for ECPS/Q 9
Stage 2.b: Recompile the software in Eclipse 11
Stage 2.c: Encrypt the Firmware 11
Stage 2.d: Convert the Programming Files 12
Stage 2.e: Program the EPCQ Flash device 13
Stage 2.f: Program the Cyclone V FPGA device 13
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �4

Stage 1.a: Configure an existing design to boot from EPCS/Q
For this lab, we will start with an EPCQ based Hardware Reference Design (HRD) project for the Arrow BeMicro CVA9 development board. The EPCQ enabled HRD project can be downloaded from the BeMicro CVA9 website page on the Altera Wiki website:
http://www.alterawiki.com/wiki/BeMicro_CV_A9 http://www.alterawiki.com/uploads/6/61/Bemicro_cv_a9_boot_from_qspi_example_15_0_2.zip
The above project employs Altera’s Serial Flash Controller IP. Be sure to read the readme.txt file. The above project is based on the second boot method described in Altera’s Application Note 736: Nios II Processor Booting From Altera Serial Flash (EPCQ)
https://www.altera.com/en_US/pdfs/literature/an/an736.pdf Configure the hardware in Qsys and then compile: 1. Open the Quartus Project, then open the cva9_qsys.qsys project in Qsys.
2. In Qsys, ensure the reset vector of the Nios II core is mapped to the EPCS/Q flash memory region, together with the relative offset in Flash Memory. For the EPCQ enabled HRD project, the reset vector offset points to 0x01E00000, an address which is located after the FPGA bitstream image.
3. In Qsys, set the “Add burstcount signal to instruction_master:” to ”Enable”. Set the “Add burstcount signal to data_master:” to “Enable”.
4. Save your Qsys Project. Click on the [Generate HDL…] button on the bottom of the Qsys window, then click on the [Generate] button in the Generation window.
5. Go to the output_files folder in your Qsys project.
a. Delete all the files (including all the .pof, .sof and .jic files) found in that folder.
6. In the Quartus Prime window, run the Compile Design task.
You MUST ensure that your initial system can successfully execute code in place from Flash before adding the inline memory encryptor! If you are not using the above mentioned EPCQ enabled HRD project, please contact your development board vendor for the most suitable baseline Qsys project with regard to executing software from flash memory. The remaining sections in stage 1 describe how to successfully execute the Bemicro_cv_a9_boot_from_qspi_example_15_0_2.zip project.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �5

Stage 1.b: Setup and compile the software in Eclipse
To setup and compile the software in Eclipse: 1. Select the Quartus Prime Window. In the menu bar click:
Tools → Nios II Software Build Tools for Eclipse
2. In the Workspace Launcher window, select the “eclipse_workspace” folder in your Qsys project.
3. The Nios II - Eclipse window will open. In the menu bar click: File → Import…
4. In the import window, click on General, then click on Existing Projects into Workspace. Click Next.
5. Click the [ Browse ] button next to the select root directly field. Select the “software” folder in your Qsys project. Click the [ OK ] button.
6. Ensure the tick box [ x ] is selected for both the led_counter folder and the led_counter_bsp folder. Click the [ Finish ] button.
7. The led_counter_bsp folder is configured to (a) boot from flash, (b) copy code and data to SDRAM, and then (c) execute from SDRAM.
a. Note: S/Labs Inline Memory Encryptor solution can be configured for:
i. Optimal low-area implementation for copying code from flash to SDRAM at boot
ii. Optimal performance implementation for executing code and data directly from flash
b. Note: You can trivially adapt this tutorial to execute code directly from flash by following the guidance provided in AN-736: Nios II Processor Booting From Altera Serial Flash (EPCQ).
8. Build the project:
a. In the Project Explorer tab, right click on led_counter_bsp. Select Nios II → Generate BSP .
i. This step regenerates the board-support package (e.g. hardware abstraction layer) .C source code files
b. In the Project Explorer tab, right click on led_counter. Select Make Targets → Build…
c. In the Make Targets window, select mem_init_generate. Click the [ Build ] button.
i. This step generates a .hex file for each of the non-volatile memories in the Qsys design. For example, the contents of the Altera Serial Flash Controller with the instantiation name “qspi_flash_controller” is stored in the “software/led_counter/mem_init/qspi_flash_controller.hex” file.
9. The project is compiled, and the .hex files should now be generated successfully.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �6

Stage 1.c: Convert Programming Files
The BeMicro CVA9 employs a Micron N25Q256A13EF8 QSPI device. This 256 Megabit QSPI device supports the Active Serial (AS) x4 configuration mode.
1. In the Quartus Prime software, go to the menu bar. Select File → Convert Programming Files to open the Convert Programming File tool.
2. Under Output programming file section, set the following items:
a. Programming file type: JTAG Indirect Configuration File (.jic)
b. Configuration device: EPCQ256
c. Mode: Active Serial x4
d. File name: led_counter.jic
e. Keep the default settings for Create Memory Map File and Create config data RPD.
f. In the input files to convert group select Flash Loader. Click on [ Add device…].
g. In the “Select Devices” window, tick [x] Cyclone V. Then tick [x] 5CEFA9. Click on [ OK ].
h. In the input files to convert group select Add Hex Data. In the Add Hex Data window:
i. Click on Absolute Addressing.
ii. In the Hex file group, click on the […] button. Navigate to the software/led_counter/mem_init folder of your Qsys project. Select qspi_flash_controller.hex file. This is the unencrypted .hex file used to program the firmware into the off-chip flash memory. Click [ Open ].
iii. Click [ OK ].
i. In this tutorial we are not going to save the FPGA bitstream to the off-chip flash.
i. In the input files to convert, select SOF Data. Click on the [ Remove ] button.
j. Click on [Save Conversion Setup…] in the Conversion setup files group at the top of the Convert Programming File tab/window. Set the value of the filename filed to: led_counters.cof . Click the [ Save ] button.
k. Click on the [ Generate ] button to generate the led_counter.jic file.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �7

Stage 1.d: Program the EPCQ Flash device1. In the Quartus Prime software, double click on Program Device (Open Programmer) in the task panel.
2. Click on the [ Hardware Setup… ] button and select the device to program.
3. Click on the [ Add File… ] button. Select led_counter.jic and click the [ open ] button.
4. Tick the [ x ] Program/Configure field beside led_counter.jic
5. Click the [ Start ] button.
6. Programming the flash device may take a minute or two.
Stage 1.e: Program the Cyclone V FPGA device1. In the Quartus Prime software, double click on Program Device (Open Programmer) in the task panel.
2. Click on the [ Add File… ] button. Navigate to the output_files folder in your Qsys project. Select the .sof file and click the [ open ] button.
3. Click on the [ Start ] button in the Programmer window.
4. Programming the FPGA device on the CVA9 board may take a minute or two.
5. If programming is successful the green LED will begin to sequentially count.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �8

Stage 2.a:Add S'Labs Inline Memory Encryptor for ECPS/Q1. Ensure S/Labs Inline Memory Encryptor IP is installed in your system, or in this quartus project’s folder
before proceeding further.
2. Open up Qsys. Find S/Labs’ Secured Off-chip Flash IP in the Qsys IP Catalog panel under: Synaptic Labs → Crypto → Secured Memory → AES Secured Off-chip Flash IP (CA-SMEM-T001).Click the [ + Add… ] button to instantiate a copy of this IP into your qsys project.
3. Configure the IP as illustrated in red circles below:
�
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �9

4. NOTE: The file browser will generate an “Absolute Path” for the .hex file. Do NOT convert the absolute path to a path that is relative to the current project folder.
5. Copy and paste the value of the Random number generated by OpenSSL into the KEY#0 field.
6. Wire up sll_ca_ssrt_smem_t001 as illustrated in the diagram below. Take special note of the regions in red boxes.
�7. In the menu bar, click on System → Assign Base Addresses.
8. Save your Qsys project.
9. In the Qsys window, click on the [ Generate HDL… ] button.
10. In the Quartus Prime window, run the Compile Design task.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �10

Stage 2.b: Recompile the software in Eclipse
Nios II software must always be recompiled after the regenerating a Qsys project: 1. Select the Eclipse Window.
2. In the menu bar of Eclipse, select Project → Clean… Ensure that [ ] Start a build immediately is not ticked.Click the [ OK ] button.
3. In the Project Explorer tab, right click on led_counter_bsp. Select Nios II → Generate BSP .
4. In the Project Explorer tab, right click on led_counter. Select Make Targets → Build…
5. In the Make Targets window, select mem_init_generate. Click the [ Build ] button.
a. This will regenerate the unencrypted .hex files corresponding to the memories that need to be initialised.
6. The project is compiled, and the unencrypted .hex files should be generated successfully.
Stage 2.c: Encrypt the Firmware1. Select the Quartus Prime Window.
2. If required, wait for the project to complete compilation.
3. In the Menu bar of the Quartus Prime window, select Tool, then select TCL Scripts.
4. Find and select the _encrypt_firmware.tcl script in the Libraries tree list view, under the Project folder.
5. Click on the “Run" button to execute that script.
6. A qspi_flash_controller_encrypted.hex file has now been generated in the software/led_counter/mem_init/ folder. In particular, the contents of
qspi_flash_controller.hex has been parsed, encrypted, and then re-encoded as
qspi_flash_controller_encrypted.hex
7. You will need to run the encrypt firmware TCL script each time you regenerate the unencrypted .hex file.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �11

Stage 2.d: Convert the Programming Files1. In the Quartus Prime software, go to the menu bar.
Select File → Convert Programming Files to open the Convert Programming File tool.
2. Click on [Open Conversion Setup…] in the Conversion setup files group at the top of the Convert Programming File tab/window. Select led_counters.cof in the Qsys Project folder. Click the [ Open ] button.
3. Change the value of the File name field from: led_counter.jic to: led_counter_encrypted.jic
4. Click on the Hex Data. Click on the [ Remove Button ] button.
5. Click on the [ Add Hex Data ] button. In the Add Hex Data window:
a. Click on Absolute Addressing.In the Hex file group, click on the […] button. Navigate to the software/led_counter/mem_init folder of your Qsys project. Select qspi_flash_controller_encrypted.hex file. This is the encrypted .hex file used to program the firmware into the off-chip flash memory. Click [ Open ].
b. Click [ OK ].
6. Click on [Save Conversion Setup…] in the Conversion setup files group at the top of the Convert Programming File tab/window. Set the value of the filename filed to: led_counters_encrypted.cof Click the [ Save ] button.
7. Click on the [ Generate ] button to generate the led_counter_encrypted.jic file.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �12

Stage 2.e: Program the EPCQ Flash device1. In the Quartus Prime software, double click on Program Device (Open Programmer) in the task panel.
2. Click on the [ Hardware Setup… ] button and select the device to program.
3. Click on the [ Add File… ] button. Select led_counter_encrypted.jic and click the [ open ] button.
4. Tick the [ x ] Program/Configure field beside led_counter_encrypted.jic
5. Click the [ Start ] button.
6. Programming the flash device on the CVA9 board may take a minute or two.
Stage 2.f: Program the Cyclone V FPGA device1. In the Quartus Prime software, double click on Program Device (Open Programmer) in the task panel.
2. Click on the [ Add File… ] button. Navigate to the output_files folder in your Qsys project. Select the .sof file and click the [ open ] button.
3. Click on the [ Start ] button in the Programmer window.
4. Programming the FPGA device on the CVA9 board may take a minute or two.
5. If programming is successful, the Nios II core will boot from encrypted firmware, and the green LED lights will begin to count sequentially in binary.
This completes the lab.
WWW.SYNAPTIC-LABS.COM 18 JANUARY 2017 VER. 01-001 PAGE �13