Mobile network layer 3
-
Upload
bheemsain-chhimpa -
Category
Documents
-
view
687 -
download
1
description
Transcript of Mobile network layer 3

Mobile Network Layer
BHEEMSAIN CHHIMPABHEEMSAIN CHHIMPA

Mobile IP
Mobile IP (IP mobility) is a protocol that is designed to allow mobile device users to move from one network to another while maintaining a permanent IP address.
The Mobile IP protocol allows location-independent routing of IP datagrams on the Internet.

Motivation for Mobile IP
Consider routing mechanisms on the internet. A host sends an IP packet with the header
containing a destination address with other fields. The destination address not only determines the receiver of the packet, but also the physical subnet of the receiver. For example, the destination address 129.13.42.99 shows that the receiver must be connected to the physical subnet with the network prefix 129.13.42. Routers in the internet now look at the destination addresses of incoming packets and forward them according to internal look-up tables.
Hence you will not receive a single packet as soon as you leave your home network, i.e., the network your computer is configured for.

Motivation for Mobile IP
Routing based on IP destination address, network prefix (e.g. 129.13.42)
determines physical subnet change of physical subnet implies change of IP address to have
a topological correct address (standard IP) or needs special entries in the routing tables
Specific routes to end-systems? change of all routing table entries to forward packets to the
right destination does not scale with the number of mobile hosts and frequent
changes in the location, security problems
Changing the IP-address? adjust the host IP address depending on the current location almost impossible to find a mobile system, DNS updates take to
long time TCP connections break, security problems

Requirements to Mobile IP Compatibility:
The installed base of Internet computers, i.e., computers running TCP/IP and connected to the internet, is huge. A new standard cannot introduce changes for applications or network protocols already in use. Mobile IP has to be integrated into existing operating systems.
Routers within the internet should not necessarily require other software. While it is possible to enhance the capabilities of some routers to support mobility, it is almost impossible to change all of them.
Mobile IP has to remain compatible with all lower layers used for the standard, non-mobile, IP. Mobile IP must not require special media or MAC/LLC protocols, so it must use the same interfaces and mechanisms to access the lower layers as IP does.
Mobile IP has to ensure that users can still access all the other servers and systems in the internet. But that implies using the same address format and routing mechanisms.

Requirements to Mobile IP Scalability and efficiency:
Introducing a new mechanism to the internet must not jeopardize its efficiency. Enhancing IP for mobility must not generate too many new messages flooding the whole network. Special care has to be taken considering the lower bandwidth of wireless links. Many mobile systems will have a wireless link to an attachment point, so only some additional packets should be necessary between a mobile system and a node in the network. Looking at the number of computers connected to the internet and at the growth rates of mobile communication, it is clear that myriad devices will participate in the internet as mobile components. Just think of cars, trucks, mobile phones, every seat in every plane around the world etc. – many of them will have some IP implementation inside and move between different networks and require mobile IP. It is crucial for a mobile IP to be scalable over a large number of participants in the whole internet, worldwide.

Requirements to Mobile IP Transparency:
Mobility should remain ‘invisible’ for many higher layer protocols and applications. Higher layers should continue to work even if the mobile computer has changed its point of attachment to the network.
Security:
Mobility poses many security problems. The minimum requirement is that of all the messages related to the management of Mobile IP are authenticated. The IP layer must be sure that if it forwards a packet to a mobile host that this host receives the packet. The IP layer can only guarantee that the IP address of the receiver is correct. There are no ways of preventing fake IP addresses or other attacks. According to Internet philosophy, this is left to higher.

The goal of a mobile IP can be summarized as:
“supporting end-system mobility while maintaining scalability, efficiency, and compatibility in all respects with existing applications and Internet protocols.”

Mobile IPEntities & Terminology Mobile Node (MN)
System (node) that can change the point of connection to the network without changing its IP address
Correspondent node (CN):
At least one partner is needed for communication. In the following the CN represents this partner for the MN. The CN can be a fixed or mobile node.
Home network:
The home network is the subnet the MN belongs to with respect to its IP address. No mobile IP support is needed within the home network.
Foreign network:
The foreign network is the current subnet the MN visits and which is not the home network.

Mobile IPEntities & Terminology Foreign agent (FA):
The FA can provide several services to the MN during its visit to the foreign network.
The FA can have the COA, acting as tunnel endpoint and forwarding packets to the MN. The FA can be the default router for the MN.
FAs can also provide security services because they belong to the foreign network as opposed to the MN which is only visiting.
For mobile IP functioning, FAs are not necessarily needed. Typically, an FA is implemented on a router for the subnet the MN attaches to.

Mobile IPEntities & Terminology
Home agent (HA): The HA provides several services for the MN
and is located in the home network. The tunnel for packets toward the MN starts at
the HA. The HA maintains a location registry, i.e., it is
informed of the MN’s location by the current COA.

Mobile IPEntities & Terminology Home agent (HA) (Cntd.)
Alternatives for the implementation of an HA:
The HA can be implemented on a router that is responsible for the home network.
If changing the router’s software is not possible, the HA could also be implemented on an arbitrary node in the subnet.
One disadvantage of this solution is the double crossing of the router by the packet if the MN is in a foreign network. A packet for the MN comes in via the router; the HA sends it through the tunnel which again crosses the router.

Mobile IPEntities & Terminology
Care-of address (COA): The COA defines the current location of the MN
from an IP point of view. All IP packets sent to the MN are delivered to the
COA, not directly to the IP address of the MN. Packet delivery toward the MN is done using a
tunnel, as explained later. To be more precise, the COA marks the tunnel endpoint, i.e., the address where packets exit the tunnel.

Mobile IPEntities & Terminology
Care of Address (Cntd.) There are two different possibilities
for the location of the COA: Foreign agent COA: The COA could be located at the
FA, i.e., the COA is an IP address of the FA. The FA is the tunnel end-point and forwards packets to the MN. Many MN using the FA can share this COA as common COA.
Co-located COA: The COA is co-located if the MN temporarily acquired an additional IP address which acts as COA.

Example network
mobile end-systemInternet
router
router
router
end-system
FA
HA
MN
home network
foreign network
(physical home networkfor the MN)
(current physical network for the MN)CN

The example network in Figure shows the following situation: A CN is connected via a router to the internet,
as are the home network and the foreign network.
The HA is implemented on the router connecting the home network with the internet, an FA is implemented on the router to the foreign network.
The MN is currently in the foreign network. The tunnel for packets toward the MN starts at the HA and ends at the FA, for the FA has the COA in this example.

IP Packet DeliveryData transfer to the mobile system
Internet
sender
FA
HA
MN
home network
foreignnetwork
receiver
1
2
3
1. Sender sends to the IP address of MN, HA intercepts packet.2. HA tunnels packet to COA, here FA, by encapsulation3. FA forwards the packet to the MN.
CN

IP Packet DeliveryData transfer from the mobile system
Internet
receiver
FA
HA
MN
home network
foreignnetwork
sender
1
1. Sender sends to the IP address of the receiver as usual, FA works as default router
CN

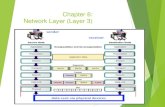
Overview
CN
routerHA
routerFA
Internet
router
1.
2.
3.
homenetwork
MN
foreignnetwork
4.
CN
routerHA
routerFA
Internet
router
homenetwork
MN
foreignnetwork
COA

Network Integration
• Three Mobile IP mechanisms– 1. Discovering the care-of address
– 2. Registering the care-of address
– 3. Tunneling to the care-of address

Network Integration
Agent Advertisement HA and FA periodically send advertisement
messages into their physical subnets MN listens to these messages and detects, if it
is in the home or a foreign network (standard case for home network)
MN reads a COA from the FA advertisement messages
Registration MN signals COA to the HA via the FA, HA
acknowledges via FA to MN these actions have to be secured by
authentication

type = 16length = 6 + 4 * #COAsR: registration requiredB: busy, no more registrationsH: home agentF: foreign agentM: minimal encapsulationG: GRE encapsulationr: =0, ignored (former Van Jacobson compression)T: FA supports reverse tunnelingreserved: =0, ignored
Agent advertisement
preference level 1router address 1
#addressestype
addr. size lifetimechecksum
COA 1COA 2
type = 16 sequence numberlength
0 7 8 15 16 312423code
preference level 2router address 2
. . .
registration lifetime
. . .
R B H F M G r reservedT

Registration
t
MN HAregistrationrequest
registration
reply
t
MN FA HAregistrationrequestregistrationrequest
registration
reply
registration
reply

Mobile IP registration request
home agenthome address
type = 1 lifetime0 7 8 15 16 312423
T x
identification
COA
extensions . . .
S B D M G r
S: simultaneous bindingsB: broadcast datagramsD: decapsulation by MNM mininal encapsulationG: GRE encapsulationr: =0, ignoredT: reverse tunneling requestedx: =0, ignored

Mobile IP registration reply
home agenthome address
type = 3 lifetime0 7 8 15 16 31
code
identification
extensions . . . Example codes:registration successful
0 registration accepted1 registration accepted, but simultaneous mobility bindings unsupported
registration denied by FA65 administratively prohibited66 insufficient resources67 mobile node failed authentication68 home agent failed authentication69 requested Lifetime too long
registration denied by HA129 administratively prohibited131 mobile node failed authentication133 registration Identification mismatch135 too many simultaneous mobility bindings

Reverse tunneling
Internet
receiver
FA
HA
MN
home network
foreignnetwork
sender
3
2
1
1. MN sends to FA2. FA tunnels packets to HA by encapsulation3. HA forwards the packet to the receiver (standard case)
CN

Why Reverse Tunneling is needed?
Firewalls
Firewalls often filter packets coming from outside containing a source address from computers of the internal network.
This avoids other computers that could use internal addresses and claim to be internal computers.
However, this also implies that an MN cannot send a packet to a computer residing in its home network.
This problem can be solved through reverse tunneling.

Why Reverse Tunneling is needed?
Multicast:
reverse tunnels are needed for the MN to participate in a multicast group.
While the nodes in the home network might participate in a multi-cast group, an MN in a foreign network cannot transmit multi-cast packets to its home network without a reverse tunnel.

Mobile IP and IPv6
Mobile IP was developed for IPv4, but IPv6 simplifies the protocols
COA can be assigned via auto-configuration. Every node has address autoconfiguration. i.e.The mechanisms for acquiring a COA are already built in.
addresses are always co-located
Every IPv6 node can send binding updates to another node, so the MN can send its current COA directly to the CN and HA. (directly to CN not via HA)
„soft“ hand-over, i.e. without packet loss, between two subnets is supported
MN sends the new COA to its old router
the old router encapsulates all incoming packets for the MN and forwards them to the new COA

Mobile ad hoc networks Standard Mobile IP needs an infrastructure
Home Agent/Foreign Agent in the fixed network
DNS, routing etc. are not designed for mobility
Characteristics of Mobile Ad hoc Network No infrastructure at all.
no default router available
every node should be able to forward
Every node should work as router
A B C

Manet: Mobile Ad-hoc Networking
FixedNetwork
MobileDevices
MobileRouter
Manet
Mobile IP
Router End system

Routing in MANET
In wireless networks with infrastructure support a base station always reaches all mobile nodes.
While in case of ad-hoc network. A destination node might be out of range of a source node transmitting packets.
Routing is needed to find a path between source and destination and to forward the packets appropriately.
In wireless networks using an infrastructure, cells have been defined. Within a cell, the base station can reach all mobile nodes.
In the case of ad-hoc networks, each node must be able to forward data for other nodes.

Routing examples for an ad-hoc network
N1
N4
N2
N5
N3
N1
N4
N2
N5
N3
good linkweak link
time = t1 time = t2

Some fundamental differencesbetween wired networks and ad-hoc wireless networks related to routing
Asymmetric links Routing information collected for one direction is of
almost no use for the other direction. However, many routing algorithms for wired
networks rely on a symmetric scenario. Redundant links
Few redundant links are required to survive link failure which are controlled by network administrator.
Where as more links are needed in MANET and there is no network administrator for controlling them.
Dynamic topology

Some fundamental differencesbetween wired networks and ad-hoc wireless networks related to routing
Asymmetric links Routing information collected for one direction is of
almost no use for the other direction. However, many routing algorithms for wired
networks rely on a symmetric scenario. Redundant links
Few redundant links are required to survive link failure which are controlled by network administrator.
Where as more links are needed in MANET and there is no network administrator for controlling them.
Dynamic topology

Traditional routing algorithmsDistance Vector Routing each node sends a routing advertisement
periodically. These advertisements contain a neighbour table with a list of link qualities like who can be reached at what distance to each neighbour.
Each node updates the local routing table according to the distance vector algorithm based on these advertisements.
Selection of the shortest path if several paths available.

Problems of traditional routing algorithms
Dynamic of the topology frequent changes of connections, connection
quality, participants .
Limited performance of mobile systems periodic updates of routing tables need energy
without contributing to the transmission of user data.
limited bandwidth of the system is reduced even more due to the exchange of routing information
links can be asymmetric, i.e., they can have a direction dependent transmission quality
Problem protocols have been designed for fixed networks
with infrequent changes and typically assume symmetric links

Dynamic source routing Split routing into discovering a path and maintaining a
path
Discover a path only if a path for sending packets to a certain destination is
needed and no path is currently available
Maintaining a path only while the path is in use one has to make sure that it
can be used continuously
No periodic updates needed!

Dynamic source routing Cntd.
Path discovery
broadcast a packet with destination address and unique ID
if a station receives a broadcast packet if the station is the receiver (i.e., has the correct destination address) then
return the packet to the sender (path was collected in the packet)
if the packet has already been received earlier (identified via ID) then discard the packet
otherwise, append own address and broadcast packet
sender receives packet with the current path (address list)

Dynamic source routing Cntd.
Optimizations
• To avoid too many broadcasts, each route request could contain a counter. Every node rebroadcasting the request increments the counter by one. Knowing the maximum network diameter (take the number of nodes if nothing else is known), nodes can drop a request if the counter reaches this number.
• A node can cache path fragments from recent requests. These fragments can now be used to answer other route requests much faster.

Interference-based routing
S1
N5
N3
N4
N1 N2
R1
R2N6
N8
S2
N9N7neighbors
(i.e. within radio range)

Clustering of ad-hoc networks
Internet
super cluster
cluster