Introduction to VPN (Virtual Private...
Transcript of Introduction to VPN (Virtual Private...
What is a Virtual Private Network (VPN)?
AVirtual Private Network allows an organisation to join theLocal Area Networks at two or more locations togetherusing an encrypted connection over the Internet. Thisallows users to securely access information wherever itmay be located on the net-work.
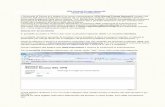
The following illustrationdepicts a very simple VPN.This would allow remote usersat an organisation's branchoffice to securely access theIT resources, such as serversand printers, at head office.
The principal advantages of aVPN over traditional computernetwork solutions are:
• Security - all data is encrypted, typically usinga 168 bit key, making it extremely secure
• Cost - replacing private circuits (leased lines) can save a considerable amount of money on an annualbasis
• Flexibility - almost all IP (Internet Protocol) traffic and hence applications can be routed through a VPN
Security
The Internet can be a dangerous place for confidentialdata. There are legions of hackers who enjoy nothing bet-ter than the challenge of penetrating other people's com-puter systems. Not all are malicious; their motives are veryvaried. However, even if information gained is not used forfraudulent purposes, the damage to company confidenceand prestige can be significant. Many hackers like to leavetheir mark upon a system or deface it to show theirprowess. Worse still they may create a "back door" intothe system, allowing them or others to easily gain accessagain at a later date.
Data sent over the Internet between two computer sys-tems will pass through many computers and network sys-tems over which the end-user has absolutely no control.Unless the data is encrypted then it is extremely vulnera-ble to being eavesdropped on.
SmoothWall Corporate Server provides a secure InternetGateway and Firewall to protect an organisation's LocalArea Networks (LANs). The SmoothTunnel andSmoothNode Add-On module establish secure encryptedVPN connections (tunnels) between Corporate ServerSystems.
Cost
Private Circuits are supplied by a TelecommunicationsCompany (TelCo) for the sole use of the customer organ-isation. They are normally subject to both installation andannual charges. The charges are normally distance relat-ed, with high capacity long distance circuits normally being
regarded as too expensive for all bar the richest corpora-tions.
Using the Internet for the long haul portion of the route isan obvious money saving scheme. It may still be neces-sary to provide short distance private circuits between thecustomer locations and the TelCo, to provide a high-speedconnection into the Internet backbone. However such aconnection could handle multiple VPN connections,instead of the traditional pattern of a dedicated circuit toeach location.
Flexibility
Internet Protocol (IP) is a family of protocols of whichTCP/IP is the best known. Most VPNs conform to a stan-dard known as IPSec that enables the VPN to carryalmost all IP protocols. Web servers, file servers, emailservers, FTP servers can all potentially be accessed fromanywhere on a VPN network, thus allowing a company torationalise its information and resources in order to preventneedles duplication. The availability of IPSec VPN clientsoftware for individual Microsoft Windows PC's means thatmobile (Road Warrior) or home workers can participate inthe company VPN, even it be from a dial-connection in anhotel bedroom.
How does a VPN Work?
Virtual Private Networking is an umbrella term thatembraces all the technologies used to secure communi-cations over the public Internet. A VPN creates "tunnels"between two VPN Gateways to protect the private data asit travels over the Internet. Tunnelling is the process ofencapsulating private IP packets into an IPSec packet; iethe private data packet is wrapped up inside the IPSecpacket like the filling in a sandwich.
© SmoothWall Limited 2002 - All trademarks are the property of their respective owners.
����������Introduction to VPN (Virtual Private Networks)
Hub
Hub
ServerServer
Branch OfficeCorporate Server Firewall
withSmoothNode Module
Corporate Server Firewallwith
SmoothTunnel Module
Head Office
Internet
Secure VPN Tunnel
WorkstationWorkstation
‘Data sent over theInternet betweentwo computer sys-tems will passthrough many com-puters and networksystems over whichthe end-user hasabsolutely no con-trol. Unless thedata is encryptedthen it is extremelyvulnerable to beingeavesdropped on.’
© SmoothWall Limited 2002 - All trademarks are the property of their respective owners.
����������A VPN Gateway is the software/hardware combinationwhich controls the VPN tunnels, its primary functionsbeing:
• Allow VPN tunnels to be configured• Authenticate the other end of a VPN connection (ie
ensure it can be identified/trusted)• Route all data received from its own local network
(LAN) to the correct VPN tunnel• Encrypt all data presented to the VPN tunnel and
encapsulate it in IPSec packets• De-encapsulate the IPSec packets received from the
VPN tunnel and de-crypt the data• Route all data received from the tunnel to the correct
computer on the local network (LAN)• Allow VPN tunnels to be managed
Once the authentication between the VPN gateways hasbeen established the tunnel is opened and the users cansend and receive data across it. There are two principalauthentication methods, Pre-Shared Key (PSK or SharedSecret) and x509 Digital Certificates (see below). A VPNGateway can normally support many VPN tunnels(depending upon licencing issues, hardware performanceand speed of the Internet connection.
What is IPSec?
The Internet Protocol Security (IPSec) protocol suite wasdeveloped by an international group organised under theauspices of the Internet Engineering Task Force (IETF).An IPSec tunnel through the Internet protects all data traf-fic passing through it, regardless of the application. Mostfirewall and VPN vendors support the IPSec standardalthough many have made their own custom extensionsto the protocol. This can make it difficult to get their sup-posedly IPSec standard equipment to interoperate withother IPSec solutions from other vendors. Microsoft hastraditionally used an alternative VPN system called Pointto Point Tunnelling Protocol (PPTP). However there are anumber of weaknesses with PPTP and it is not generallyconsidered to be very secure; the reason why virtuallyeverybody else uses IPSec. Corporate Server will allowPPTP traffic to pass through or be forwarded by the fire-wall but it will not act as a PPTP gateway or client.
What are x509 Certificates?
Each VPN tunnel will normally be individually authenticat-ed using digital certificates (x509 certificates). The certifi-cates come in two parts, the private and the public part.Each end of the VPN tunnel must have the public part ofthe other ends x509 certificate. The certificate, in the formof a computer file, is an electronic document that like a driv-ing license identifies its owner. The certificate should beunique, eg the Miami branch office certificate. For RoadWarriors this should be a personal certificate. So when theMiami office goes to establish and authenticate the VPNtunnel to the Head Office VPN Gateway in New York, it islooking to be receive the public part of the New York cer-tificate and no other. Conversely New York will expect theMiami certificate. If the certificate exchange is not asexpected then the tunnel will not be opened. This guaran-tees that each end can trust the other. Digital certificatescan be leased from companies like Verisign or Thawte,
can be created by Certificate Authorities such as the oneincluded in Microsoft Windows 2000™, or more conve-niently, using SmoothTunnel's in-built Certificate Authority(CA).
What is wrong with Pre-Shared Key (PSK, SharedSecret) Authentication?
PSK authentication basically pre-dates x509 certificateauthentication. With PSK a pass phrase is configured atboth ends of the VPN connection. The authenticationbasically consists of comparing the two pass phrases - ifthey match then the VPN tunnel has been authenticatedand is opened. This is obviously nothing like as secure asthe exchange of x509 certificate information, where thecertificates (files) have to be created on the sameCertificate Authority. A Pre-Shared Key can be dictatedover the phone so is liable to being eavesdropped, pluslike many passwords, people often choose easy toremember and hence insecure phrases.
PSK certainly works and almost all VPN solutions supportit - so it is often used as away to connect systems from dif-ferent manufacturers. X509 certificates are undoubtedly amore robust authentication method. X509 certificates canbe re-issued when necessary and be rescinded if say anemployee leaves the company. This is especially impor-tant for a VPN solution supporting Road Warriors. It isbasically impracticable to construct a Road Warrior VPNsystem using PSK, principally as each Road Warriorwould need the same shared-secret, thus if one personleaves the company then all users would need to changetheir shared-secret. Perhaps a secret shared so widely willnot be secret for very long!
What are DES and 3DES?
DES is an acronym for the Data Encryption Standard.This is a US government standard for the encryption ofcommercial data. It uses a 64-bit key and is nowadaysconsidered not to be particularly secure.
Most VPN solutions now use the Triple Data EncryptionStandard (3DES, pronounced triple DES) which is definedby ANSI standard X9.52. The data is effectively encrypt-ed three times, typically using a 168-bit encryption key.This means that it will require a huge amount of time andcomputer power to de-encrypt the data without knowingthe key in advance. It must be accepted that nothing istotally secure, all that we can do is to take sensible andrealistic precautions. If the CIA decides its wants to inter-cept your data and is prepared to put a considerableamount of time and money into doing so, it will succeed.However to make things more difficult for potential crack-ers, the keys are changed every few hours, so even ifsomebody should work out a key then it is only of use fora short period of time.
SmoothTunnel
SmoothTunnel is the VPN Gateway module for CorporateServer. It:
• Forms the central point of a small VPN network• Incorporate a Certificate Authority (CA) to create and
issue self-signed x509 certificates
‘Most firewall andVPN vendors sup-port the IPSec stan-dard althoughmany have madetheir own customextensions to theprotocol. This canmake it difficult toget their supposed-ly IPSec standardequipment to inter-operate with otherIPSec solutionsfrom other ven-dors.’
‘X509 certificatesare undoubtedly amore robustauthent ica t ionmethod.‘
© SmoothWall Limited 2002 - All trademarks are the property of their respective owners.
����������• Supports from 5 to 100 or more active VPN tunnels (depending upon hardware and Internet connectionsspeed)
• Hosts VPN connections to SmoothNode Systems (single tunnel variant of SmoothTunnel)
• Can establish VPN connections to other SmoothTunnel Systems
• Supports VPN connections from Road Warriors usingIPSec VPN Clients for Microsoft Windows™
• Can establish VPN connections to other IPSec compliant systems
There must be at least one SmoothTunnel module in aSmoothWall VPN network.
SmoothTunnel supports VPN connections from systemsusing Dynamic IP addresses, such as SmoothNode orRoad Warrior VPNclients. SmoothTunnelitself can utilise aDynamic DNS name toidentify the VPN gate-way instead of a fixedIP address, again facili-tating the use of aDynamic IP address orallowing the VPN gate-way to be moved toanother Internet con-nection in the event of aline/router failure.
In a more complex net-work with regional cen-tres requiring VPN con-nections to both branchoffices and a centralHead Office, both Head Office and the regional centreswould need SmoothTunnel to support the multiple VPNconnections. SmoothNode would still adequately servethe branch offices, at the end of the VPN network.
SmoothConnection
SmoothConnection is a license to increase the number ofVPN tunnels that can be configured on a SmoothTunnelVPN gateway. As standard SmoothTunnel allows five (5)VPN connections to be configured. This can be extendedby the purchase of SmoothConnection License packs,which add another 5, 10, 20 or 50 tunnels each. Thepacks can be stacked, so that adding both a 10 and a 20tunnel pack will raise the total tunnel count to 35 (includingthe five (5) that come as standard with SmoothTunnel).
SmoothNode
SmoothNode is in effect a cut-down derivative ofSmoothTunnel for use where only a single VPN connec-tion is required. A typical example of its use is in a branchoffice network. Each branch offices would be equippedwith Corporate Server and the SmoothNode module,which will establish a single VPN tunnel back toSmoothTunnel VPN Gateway at Head Office.SmoothNode does not incorporate a Certificate Authorityso cannot create x509 certificates; it must utilise a certifi-cate created elsewhere, typically by SmoothTunnel'sCertificate Authority. SmoothNode cannot support a RoadWarrior Connection, only SmoothTunnel can do this. In allother respects SmoothNode offers the same functionalityand performance as SmoothTunnel. SmoothNode can be
used on a system that has a dynamic IP address, savingthe need to provide a static (fixed) IP address.
Road Warriors
If only a single remote PC needs to connect to the VPNGateway (SmoothTunnel) we class this as a Road Warrior.The term springs from travelling salesmen, managers - infact anybody requiring computer access from a non-fixedlocation. However we encompass within this term mosthome workers, as typically they have only a single comput-er they use for work, rather that a small network (LAN) aswould be found in a branch office.Road Warrior/Home User PCs will need an IPSec VPNclient for Microsoft Windows™. We recommend theSafeNet SoftRemote IPSec VPN client. It works well withSmoothTunnel and of the products we have tested has
proved to be the easiest to set-up and get working.SoftRemote supports Windows 95, 98, ME, NT4, 2000and XP. Although Microsoft Windows 2000™ andWindows XP™ include IPSec software we do not classthis as a Road Warrior IPSec client. The reasons are thatit does not support dynamic IP addresses and is general-ly considered to be too complex to set-up and use for RoadWarriors. We class it as a VPN gateway, not a client.
Consideration must be given to protecting these RoadWarrior PCs from hackers and viruses - the VPN tunnel toHead Office will be secure but if they communicate on theInternet outside of the VPN tunnel then there are risks tobe borne in mind.
IP address is essential for use with multiple sub-net net-works; otherwise the Road warrior would not be able toconnect to servers on all sub-nets.
Having tested a number of IPSec clients for MicrosoftWindows™, we have found SoftRemote from SafeNetSystems Inc. to be the easiest to install, configure and getworking.
Example Network
The following diagram depicts part of a VPN for a largemulti-office organisation.
The organisation's Head Office is at the centre of the dia-gram. It has direct VPN connections to two branch(remote) offices (Aand B), at the top left and top right of thediagram. The users at these branch offices would be ableto access the corporate ITservices at Head Office, such as
Application
Server
Head OfficeCorporate Server Firewall
withSmoothTunnel Module
Road Warrior
Modem
(or ADSL, ISDN)
Microsoft Windows PC
with IPSec VPN Client
Corporate Ethernet Network
Server
Internet
Secure VPN Tunnel
Workstation
‘SmoothTunnelsupports VPN con-nections from sys-tems usingDynamic IPaddresses, such asSmoothNode orRoad Warrior VPNclients.’
© SmoothWall Limited 2002 - All trademarks are the property of their respective owners.
����������
email, Intranet, file and application servers. Effectively theycan work and share data as though they were physicallypresent at Head Office. The speed of operation woulddepend upon the speed of the Internet connections at boththe Head Office and the Branch office. Normally such aHead Office would have a short distance private circuit
(leased line) to connect it to their Internet Service Provider(ISP). This will ensure that a fixed bandwidth (speed)available and is normally subject to a Service LevelAgreement to guarantee uptime and time to repair if a faultdevelops. Failure of the Internet connection to Head Officewould cause disruption to the entire organisation, whereasfailure of the Internet connection to a branch office wouldhave little effect upon the rest of the organisation. TheHead Office supports multiple VPN connections so usesthe SmoothTunnel module, which acts as the CertificateAuthority (CA) for the entire network.The branch offices may be connected to the Internet usingADSL, contending for bandwidth with the other users intheir ADSL group (the TelCo will publish the contentionratios for its ADSLservices). Thus there will be no perform-ance guarantee, nor will the TelCo normally offer a ServiceLevel Agreement. However ADSL normally costs a frac-tion of the price of a leased line connection so can be verycost effective.
The Head Office also connects to a Regional (Area) Office(bottom centre), which in turn connects to Branch Office Cat the bottom right of the diagram. This, for example rep-resents an international organisation, where branch (coun-try) offices report to a regional office and in turn, the region-al offices report back to Head Office. The Regional Officehas the SmoothTunnel module, as it needs to support mul-tiple VPN connections, ie to its branch offices and HeadOffice.
The network also illustrates a Road Warrior who can opena VPN connection from their notebook PC using a dial-up(modem) connection to the corporate data centre at HeadOffice. The organisation's network also supports Home
Workers who connect to Regional Offices. ADSL wouldprobably be the first choice for these connections withISDN, satellite, wireless or analogue modem being thealternatives, mainly dependent upon geographic location.Depending upon how the VPN tunnels are configured,users can "tunnel through" one SmoothWall system to
another network.
Depending upon how the VPNtunnels are configured, userscan "tunnel through" oneSmoothWall system to anothernetwork. Branch Offices AandB could for instance access theservers at the Regional Office,so there is no need to configurea VPN tunnel between eachlocation which needs to shareresources. However the twobranch offices "tunnellingthrough" Head Office will obvi-ously consume bandwidth (inand back out again) andincrease the workload upon theHead Office Corporate Server.For occasional usage this isprobably sensible but if fre-quently used then a direct VPNtunnel would probably be pro-vided. It should also be bornein mind that "tunnelling through"can present a security risk, itmay not be desirable for
branch office users to gain access to the systems at otherbranch offices etc. Thus this aspect needs careful consid-eration to user limit access.
Branch Office C has a direct VPN tunnel back to HeadOffice to provide a degree of redundancy should the con-nection to its Regional Office fail. Although the above dia-gram represents a relatively simple star network, crosslinks can be added where required to provide both directtunnels avoiding "tunnelling through" and increase redun-dancy in the event of failure somewhere in the network. AsBranch Office C has two VPN tunnels it will need theSmoothTunnel module.
Hardware Requirements
Corporate Server will run on virtually any Pentium classmachine. However in the case of a SmoothTunnel VPNgateway supporting several VPN tunnels, we normallyrecommend that the machine specification meets orexceeds a Pentium III 500 MHz, with 64 MBytes RAM and4 GBytes hard disk. Reputable (branded) Ethernet cardsare also strongly recommended. Such a specificationshould be capable of supporting 50 VPN tunnels.SmoothNode can operate on a minimum specificationsystem, ie Pentium with 32 MBytes RAM and 250 MByteshard disk.
Branch Office B
Corporate ServerFirewall
withSmoothTunnel Module
Head Office
CorporateServer Firewall
withSmoothTunnel
Module
Branch Office C
Server
CorporateServer Firewall
withSmoothNode
Module
Branch Office A
Regional
Office
Corporate ServerFirewall
withSmoothTunnel
Module
Road Warrior
Microsoft Windows PC, Integral
PCMIA Modem and IPSec VPN
Client
Home Worker
ADSL,
ISDN or Modem
CorporateServer Firewall
withSmoothNode
Module
SmoothWall LimitedSuite 325, 80 High StreetWinchester, HampshireSO23 9AT, UKTel: +44-(0)7092-377632Fax: +44-(0)113-203-7352
Email: [email protected]
WWW:www.smoothwall.co.uk