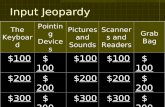
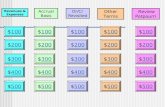
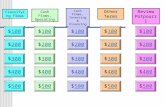
I T Essentials I Chapter 9 JEOPARDY TechnologySecurityThreatsSecurityMaintenancePotpourri 100100 200...
-
Upload
kory-moody -
Category
Documents
-
view
218 -
download
1
Transcript of I T Essentials I Chapter 9 JEOPARDY TechnologySecurityThreatsSecurityMaintenancePotpourri 100100 200...
TechnologyTechnologySecuritySecurityThreatsThreats
SecuritySecurity MaintenanceMaintenance Potpourri Potpourri
100 100 100 100 100
200 200 200 200 200
300 300 300 300 300
400 400 400 400 400
500 500 500 500 500
Technology100
Which technology is used for authenticating users?
1. Event Viewer2. Secure DNS3. Smart Card4. UNC
A: What is smart card?
Technology200
A fingerprint reader is an example of which security technology?
1. Authorization2. Biometric3. Keylogging4. Secureware5. smartcard
A: What is biometric?
Technology300
Technology created by Microsoft to control interactivity on web pages?
1. JAVA2. Visual Basic3. Active X4. JAVA Script
A: What is Active X?
Technology 400
What are the primary responsibilities of a technician?1. Assembling and networking computers2. Customer service3. Data and network security4. Implementing cost saving procedures
A: What is data and network security?
Technology500
What is an e-mail bomb?1. A series of repeated, larger than normal pings that
crash the receiving computer2. A large quantity of bulk e-mail that overwhelms the
e-mail server preventing users from accessing it3. Programming language that allows applets to run
within a web browser4. Technology created by Microsoft to control
interactivity on web pages.
A: What is Option 2?
Security Threats100
A: What is adware?
What type of program causes banners and ads to appear on the desktop without any user intervention?
1. Adware2. Spyware3. Stealth virus4. Trojan horse
Security Threats 200
A: What is spyware and grayware?
What are two examples of malware?1. Registry cleaner2. Pop-up blocker3. Spyware4. E-mail5. Grayware
Security Threats 300
A: What is options 2 & 5?
Which two characteristics describe a worm?1. Executes when software is run on a computer2. Is self-replicating3. Hides in a dormant state until needed by an attacker4. Infects computers by attaching to software code5. Travels to new computers without any intervention or
knowledge of the user
Security Threats 400
A: What is social engineering?
An employee for a small company inadvertently allows a visitor to see their username and password. At home, the visitor then uses this information to gain access to the company network. What type of threat is this?
1. Man-in-the-middle2. Phishing3. Physical4. Social engineering5. spoofing
Security Threats 500
A: What is DDoS?
Which threat to security uses traffic from zombie computers to overwhelm servers?
1. DoS2. DDoS3. Phishing4. Spoofing5. SYN flood
Security100
What is options 1 & 4?
Which two statements are true regarding username and password standards?
1. Keep the username naming convention simple2. Usernames should expire periodically3. Keep the passwords simple and easy to remember4. Rules about password expiration & lockout should be
defined5. Users should create their own username and password
Security 200
A: What is Disable SSID broadcast?
When setting up a new wireless access point, which basic security measure should be taken?
1. Disable SSID broadcast2. Enable SSID broadcast3. Broadcast the default SSID4. Broadcast a unique SSID
Security 300
A: What is phishing?
An attacker claiming to be a bank representative contacts a potential victim via e-mail and requests disclosure of vital account information. Which security attack is being implemented?
1. Adware2. Phishing3. Spyware4. Trojan
Security 400
A: What is use a VPN connection?
What is the best method for a company to secure data being transmitted across the internet between remote sites?
1. Use plain text in an e-mail2. Use a shared server with an encrypted password on
the file3. Use computers secured with smartcard authentication4. Use a VPN connection
Security 500
A: What is option 3 – Security cage?
Which is the best way to secure a laptop left at the office while the user is away for an extended period of time?
1. Cover the laptop with files and leave it on your desk2. Put the laptop in a desk drawer in your locked office3. Place the laptop in a locked security cage designed to
store computer equipment4. Hide the laptop in your supervisor’s office
Maintenance100
What is Offsite secure facility
What is the safest place to store backups?1. Portable lock box2. Locked telecommunications room3. Locked server room4. Offsite secure facility
Maintenance200
A: What is download latest signature files on a regular basis?
What must be done to ensure that the anti-virus software on a computer is able to detect and eradicate the most recent viruses?
1. Download the latest signature files on a regular basis2. Schedule a scan once a week3. Schedule anti-virus updates using windows task
manager4. Follow the firewall configuration guidelines on the
anti-virus manufacturer website.
Maintenance 300
A: What is options 2 & 3?
Which two items can be downloaded from the Microsoft website to help protect Windows XP?
1. ROM upgrades2. Service packs3. Security patches4. BIOS upgrades5. DirectX updates
Maintenance 400
A: What is destroy the hard drives with a hammer?
A bank is upgrading the hard drives in a server. What should be done to the old hard drives to permanently remove any confidential data?
1. Delete the files containing the confidential data2. Reformat the hard drives3. Expose the hard drives to ultraviolet light4. Destroy the hard drives with a hammer
Maintenance 500
What is create a restore point
A technician downloaded the latest Windows XP updates from the Microsoft website. What should the technician do before installing the updates?
1. Create a restore point2. Manually update the last know good configuration3. Reinstall the anti-virus software4. Change the firewall rules to enable the installer to
access a port 8900 of the Microsoft server
Potpourri100
A: What is Option 4?
What is the difference between WEP64 and WEP 128?
1. WEP64 can handle 64 simultaneous connections, & WEP128 can handle 128 simultaneous connections.
2. WEP64 operates on a 64-bit processor, but WEP128 requires a dual core 128-bit processor
3. WEP64 uses 64-byte packets, and WEP128 uses 128-byte packets
4. WEP64 uses a 64-bit encryption key, and WEP uses a 128-bit key.
Potpourri200
A: What is option 3?
Which best practice should be included in a password protection policy?
1. Encourage users to document passwords in a personal file
2. Enforce password protection at the BIOS level3. Implement lockout rules upon consecutive
unsuccessful attempts at accessing the system4. Restrict passwords to text-bases strings
Potourri300
A: What is False?
The value of physical equipment is often of far more than the value of the data it contains.
1. True2. False
Potpourri400
A: What is VPN?
What network uses encryption to protect data?1. Wireless2. VPN3. WEP4. Star
Potpourri500
A: What is FAT32?
What file system used in some versions of Windows lacks both journaling and encryption capabilities?
1. NTFS2. FAT323. FAT 164. NTFS2
Double Jeopardy
A: What is Patches?
Manufacturers of operating systems and software applications may provide code updates called __________ that prevent a newly discovered virus or worm from making a successful attack.1.Signatures2.patches3.Service pack4.SYN flood