OPeNDAP/HTTP Security Issues John Caron Unidata. ClientServer GET HTTP/1.x 401 Unauthorized :
Clientserver Notes
-
Upload
kannan-kumaran -
Category
Documents
-
view
214 -
download
0
Transcript of Clientserver Notes
-
8/11/2019 Clientserver Notes
1/43
UNIT - III
Database Server:
A database server is a computer program that provides database services to other computer programs or computers, as defined by the client server model. The term may also refer to acomputer dedicated to running such a program. Database management systems frequently
provide database server functionality, and some DBMSs (e.g., MySQL) rely exclusively on theclient server model for database access.
Such a server is accessed either through a "front end " running on the users computer whichdisplays requested data or the " back end" which runs on the server and handles tasks such as dataanalysis and storage.
In a master-slave model, database master servers are central and primary locations of data whiledatabase slave servers are synchronized backups of the master acting a sproxies.
Most of the Database servers works with the base of Query Language. Each Databaseunderstands its query language and converts it to Server readable form and executes it to retrievethe results.
Some examples of proprietary database servers are Oracle, DB2, Informix, and Microsoft SQLServer. Examples of GNU General Public Licence database servers are Ingres and MySQL. Every server uses its own query logic and structure. The SQL query language is more or less thesame in all relational database servers. DB-Engines lists over 200 DBMSs in its ranking.
What Soes Data Base Server DO:
We all use tens and hundreds of different websites on a daily basis and most of them usedatabases to collect and store the data.Have you ever asked yourself how do database servers work ?I know this is silly question for technical users, but I am sure not everyone knows the answer tothis.Let me start with the basic definition of a Database and Database Server. A database is acollection of information that is organized so that it can easily be accessed, managed, andupdated. A database server is a computer program that provides database services to othercomputer programs or computers using a client-server model. The term may also refer to acomputer dedicated to running such a program.
Also, you should know that there are many different types of database server softwares. Someare open source (ie. MySQL, MongoDB, PostgresSQL) and some are commercial software (ie.MSSQL, Oracle).
Now that we know what the Database Server term means, lets explore the communication process of the client-server model.The process is not that complicated. Imagine that some computer has contently running programthat can understand some special language (SQL or Structured Query Language), but only listens
http://en.wikipedia.org/wiki/Computer_programhttp://en.wikipedia.org/wiki/Databasehttp://en.wikipedia.org/wiki/Computerhttp://en.wikipedia.org/wiki/Client%E2%80%93serverhttp://en.wikipedia.org/wiki/Client%E2%80%93serverhttp://en.wikipedia.org/wiki/Client%E2%80%93serverhttp://en.wikipedia.org/wiki/Software_modelinghttp://en.wikipedia.org/wiki/Database_management_systemhttp://en.wikipedia.org/wiki/Database_management_systemhttp://en.wikipedia.org/wiki/MySQLhttp://en.wikipedia.org/wiki/Front_and_back_endshttp://en.wikipedia.org/wiki/Front_and_back_endshttp://en.wikipedia.org/wiki/Front_and_back_endshttp://en.wikipedia.org/wiki/Master-slave_(technology)http://en.wikipedia.org/wiki/Proxy_serverhttp://en.wikipedia.org/wiki/Oracle_Databasehttp://en.wikipedia.org/wiki/IBM_DB2http://en.wikipedia.org/wiki/Informixhttp://en.wikipedia.org/wiki/Microsoft_SQL_Serverhttp://en.wikipedia.org/wiki/Microsoft_SQL_Serverhttp://en.wikipedia.org/wiki/GNU_General_Public_Licencehttp://en.wikipedia.org/wiki/Ingres_(database)http://en.wikipedia.org/wiki/MySQLhttp://en.wikipedia.org/wiki/MySQLhttp://en.wikipedia.org/wiki/Ingres_(database)http://en.wikipedia.org/wiki/GNU_General_Public_Licencehttp://en.wikipedia.org/wiki/Microsoft_SQL_Serverhttp://en.wikipedia.org/wiki/Microsoft_SQL_Serverhttp://en.wikipedia.org/wiki/Informixhttp://en.wikipedia.org/wiki/IBM_DB2http://en.wikipedia.org/wiki/Oracle_Databasehttp://en.wikipedia.org/wiki/Proxy_serverhttp://en.wikipedia.org/wiki/Master-slave_(technology)http://en.wikipedia.org/wiki/Front_and_back_endshttp://en.wikipedia.org/wiki/Front_and_back_endshttp://en.wikipedia.org/wiki/MySQLhttp://en.wikipedia.org/wiki/Database_management_systemhttp://en.wikipedia.org/wiki/Database_management_systemhttp://en.wikipedia.org/wiki/Software_modelinghttp://en.wikipedia.org/wiki/Client%E2%80%93serverhttp://en.wikipedia.org/wiki/Computerhttp://en.wikipedia.org/wiki/Databasehttp://en.wikipedia.org/wiki/Computer_program -
8/11/2019 Clientserver Notes
2/43
someone specific (security measure) rather than everyone who tries to talk to it. Now whensomeone who is allowed to talk to Database Server sends it a command, the command will be
processed and necessary data selected or updated from/to database storage and result send backto requester.Different types of database servers use different data storage techniques (also called engines) andusually can utilize multiple engines at the same time depending on your needs. In most cases, alldata is physically stored as files on the same computer where the database server is running, oron any remote storage.
SQL & What Does SQL Do
What is SQL?
SQL was initially developed at IBM by Donald D. Chamberlin and Raymond F. Boyce in theearly 1970s .[13] This version, initially called SEQUEL (Structured English Query Language ), was
designed to manipulate and retrieve data stored in IBM's original quasi-relational databasemanagement system, System R, which a group at IBM San Jose Research Laboratory haddeveloped during the 1970s .[13] The acronym SEQUEL was later changed to SQL
What Can SQL do?
SQL can execute queries against a database SQL can retrieve data from a database SQL can insert records in a database SQL can update records in a database SQL can delete records from a database SQL can create new databases SQL can create new tables in a database SQL can create stored procedures in a database SQL can create views in a database SQL can set permissions on tables, procedures, and views
Operators [edit]
Operator Description Example
= Equal to Author = 'Alcott'
Not equal to (most DBMS also Dept 'Sales'
http://en.wikipedia.org/wiki/IBMhttp://en.wikipedia.org/wiki/Donald_D._Chamberlinhttp://en.wikipedia.org/wiki/Raymond_F._Boycehttp://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/IBM_System_Rhttp://en.wikipedia.org/wiki/IBM_Almaden_Research_Centerhttp://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/w/index.php?title=SQL&action=edit§ion=4http://en.wikipedia.org/w/index.php?title=SQL&action=edit§ion=4http://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/IBM_Almaden_Research_Centerhttp://en.wikipedia.org/wiki/IBM_System_Rhttp://en.wikipedia.org/wiki/SQL#cite_note-chamberlin-boyce-sequel-13http://en.wikipedia.org/wiki/Raymond_F._Boycehttp://en.wikipedia.org/wiki/Donald_D._Chamberlinhttp://en.wikipedia.org/wiki/IBM -
8/11/2019 Clientserver Notes
3/43
accept != instead of )
> Greater than Hire_Date> '2012-01-31'
< Less than Bonus < 50000.00
>= Greater than or equal Dependants>= 2
-
8/11/2019 Clientserver Notes
4/43
Conditi onal (CASE) expressions [edit]
SQL has the case/when/then/else/end expression, which was introduced in SQL-92. In its most
general form, which is called a "searched case" in the SQL standard, it works like else if in other programming languages:
CASEWHEN n >0THEN 'positive'WHEN n
-
8/11/2019 Clientserver Notes
5/43
UPDATE exampleSET field1 ='updated value'WHERE field2 ='N';
DELETE removes existing rows from a table, e.g.:
DELETEFROM exampleWHERE field2 ='N';
MERGE is used to combine the data of multiple tables. It combines
the INSERT and UPDATE elements. It is defined in the SQL:2003 standard; prior to that,
some databases provided similar functionality via different syntax, sometimes called"upsert" .
MERGEINTOTABLE_NAMEUSING table_reference ON (condition)WHEN MATCHED THEN UPDATESET column1 = value1 [, column2 = value2 ...]WHENNOT MATCHED THEN INSERT (column1 [, column2 ...]) VALUES (value1 [, value2 ...
STORED PROCEDURES:
A stored procedure is a batch of Transact-SQL (T-SQL) code that is saved internally in SQLServer. Stored procedures can be used to mask complex SQLtasks from clients, improve the
performance of your application, enforce data and business rules, increase multi-user
concurrency, and reduce locking and blocking conflicts.
USES FOR STORED PROCEDURES
There are other good reasons to use stored procedures besides speed:
Reduced utilization of network ba ndwidth. Stored procedures can optimize data access byreturning limited result sets. Users can be prevented from executing queries that choke the serveror the network.
Errors can be handled at the server, in the stored procedure, and not at the client.
Security permissions can be removed from tables, preventing direct table access. Users canexecute stored procedures that work with tables they do not have permissions on as long as bothstored procedure and table have the same owner.
A stored procedure is written once, and can be accessed from many client applications.
Stored procedures reduce the complexity of cli ent coding.
http://en.wikipedia.org/wiki/Delete_(SQL)http://en.wikipedia.org/wiki/Merge_(SQL)http://en.wikipedia.org/wiki/Upserthttp://en.wikipedia.org/wiki/Upserthttp://en.wikipedia.org/wiki/Merge_(SQL)http://en.wikipedia.org/wiki/Delete_(SQL) -
8/11/2019 Clientserver Notes
6/43
Stored procedures divorce the cli ent application from the table structure. Clients dont need toknow anything about the database except the input and output structure of the stored procedure.Thus, changes can be made to database structures without breaking client code
STORED PROCEDURE SYNTAX
Heres the syntax fo r creating a stored procedure:
CREATE PROC[EDURE] procedure_name [; number]
[{@parameter data_type}
[VARYING] [= default] [OUTPUT]
] [,...n]
[WITH
{RECOMPILE | ENCRYPTION | RECOMPILE , ENCRYPTION}]
[FOR REPLICATION]
AS sql_statement [...n]
TRIGGER:
Triggers are procedures that run automatically in response to changes to your data. The primary purpose of a trigger is to make a decision as to whether these data changes should be committed
to the database, but they can perform any type of data manipulation action. There are threestandard types of
triggers: INSERT, UPDATE, and DELETE. In SQL Server 2000, a new type
was added INSTEAD OF. While earlier versions of SQL Server only
supported a single trigger of each type per table, SQL Server 7.0 supports
multiple triggers on the same table, and in SQL Server 2000 you can even
control which triggers fire first and last.
NOTE There is no such thing as a SELECT trigger. Triggers only exist
for data modification operations such as insert, update, and delete.
USES FOR TRIGGERS
-
8/11/2019 Clientserver Notes
7/43
Triggers are often used to enforce business rule s that cant be expressed as a constraint, and toraise alerts. There are some business rules that are too complex to be implemented within theexpressions available for constraints or rules. Triggers can reference values from any othercolumn in the affected record, including the original and the changed values, and triggers canalso reference data in other tables or other databases. One reason to use a trigger is if you need toenforce a relationship between tables that are in separate databases, since DRI cannot be used forthis. Like stored procedures, triggers can contain complex logic, variables, error handling, andalmost the full range of Transact-SQL programming. The only limitation on your Transact-SQLcode in triggers is that you cannot create objects or modify their design, and you cannot performadministrative tasks like backups.HOW TRIGGERS WORK
A trigger uses two virtual tables named inserted and deleted to do most of its work. When SQLServer fires an INSERT trigger, it copies the new values into the inserted table. For an UPDATEtrigger, the new value is also copied to inserted, and the old value is copied to deleted. And ofcourse for a DELETE trigger, the value being deleted is copied to deleted. Triggers can alsoreference other objects, and you can join other tables to the inserted and deleted tables. Forexample, to create an audit trail, you could create a trigger that inserts the values contained in thedeleted table into a backup table and perhaps adds the name of the current user and the currentdate and time. Since the trigger fires each time a row is deleted, no further action is necessary.You can create triggers for both tables and views. Triggers created for tables will fire wheneverthe data in the table is modified. Triggers on views, however, only fire if the data modification isdone through that view, and the only kinds of triggers you can create for views are INSTEADOF triggers.
TRIGGER SYNTAX
The syntax for triggers is very much the same as for a stored procedure. The primary difference between a stored procedure and a trigger is how the object is executed. Stored procedures areexplicitly called, while triggers are fired automatically in response to a data modification.
CREATE TRIGGER trigger_name
ON {table|view}
[WITH ENCRYPTION]
{
{{FOR|AFTER|INSTEAD OF} {[DELETE][,][INSERT][,][UPDATE]}
[NOT FOR REPLICATION]
AS
-
8/11/2019 Clientserver Notes
8/43
[{IF UPDATE(column)
[{AND|OR} UPDATE(column)]
[...n]
| IF (COLUMNS_UPDATED() {bitwise_operator}
updated_bitmask)
{comparison_operator} column_bitmask [...n]
}]
sql_statement [...n]
}
}
RULES:
The last option is to perform partitioning using rules, which are based on plan rewriting(compared to procedural triggers). For each partition a separate rule is created using a commandsimillar to this:
CREATE OR REPLACE RULE rule_100000 AS ON INSERT TO table_baseWHERE (id > 0 AND id
-
8/11/2019 Clientserver Notes
9/43
DATA WAREHOUSES:
Overview A data warehouse is the concept of data extracted from operational systems and made availableas historical snapshots for ad-hoc queries and scheduled reporting. Characteristics that
distinguish data in the data warehouse from data found in the operational environment are that itis: organized in such as way that relevant data is clustered together for easy access, severalcopies of the data from various points in time are kept together, and once the data is placed intothe data warehouse it is not updated. Rather, the historical snapshots stored in the DataWarehouse are periodically refreshed with data from the operational databases.The main problem addressed by a data warehouse is that end-users have a difficult time
producing ad-hoc or other specialized queries and reports. This is due to several factors: Most of the data is stored in ADABAS, which is difficult for end-users to access. The data stores were designed for transaction processing not ad-hoc reporting. Obtaining the data or a report usually requires waiting for a programmer to either develop the
report or provide a customized download program. All of the data may not be consistent as of the same point in time. There may not be enough copies of the data kept for historical reporting in the operational
systems. End-users do not have the knowledge of what is kept in the existing data stores.AdvantagesThe data warehouse addresses these factors and provides many advantages to the end-users ofthe University including: Improved end-user access to a wide variety of University data Increased data consistency Additional documentation of the data Potentially lower computing costs and increased productivity Providing a place to combine related data from separate sources Creation of a computing infrastructure that can support changes in computer systems and
business structures.Empowering end-users to perform any level of ad-hoc queries or reportswithout impacting the performance of the operational systems.
OLTP:
Online transaction processing , or OLTP , is a class of information systems that facilitate andmanage transaction-oriented applications, typically for data entry and retrieva ltransaction
processing. The term is somewhat ambiguous; some understand a "transaction" in the context ofcomputer or database transactions, while others (such as th eTransaction Processing PerformanceCouncil) define it in terms of business or commercial transactions. OLTP has also been used torefer to processing in which the system responds immediately to user requests. An automatedteller machine (ATM) for a bank is an example of a commercial transaction processing
http://en.wikipedia.org/wiki/Information_systemhttp://en.wikipedia.org/wiki/Transaction_processinghttp://en.wikipedia.org/wiki/Transaction_processinghttp://en.wikipedia.org/wiki/Database_transactionshttp://en.wikipedia.org/wiki/Transaction_Processing_Performance_Councilhttp://en.wikipedia.org/wiki/Transaction_Processing_Performance_Councilhttp://en.wikipedia.org/wiki/Financial_transactionhttp://en.wikipedia.org/wiki/Automated_teller_machinehttp://en.wikipedia.org/wiki/Automated_teller_machinehttp://en.wikipedia.org/wiki/Automated_teller_machinehttp://en.wikipedia.org/wiki/Automated_teller_machinehttp://en.wikipedia.org/wiki/Financial_transactionhttp://en.wikipedia.org/wiki/Transaction_Processing_Performance_Councilhttp://en.wikipedia.org/wiki/Transaction_Processing_Performance_Councilhttp://en.wikipedia.org/wiki/Database_transactionshttp://en.wikipedia.org/wiki/Transaction_processinghttp://en.wikipedia.org/wiki/Transaction_processinghttp://en.wikipedia.org/wiki/Information_system -
8/11/2019 Clientserver Notes
10/43
-
8/11/2019 Clientserver Notes
11/43
While academics have perceived DSS as a tool to support decision making process, DSS userssee DSS as a tool to facilitate organizational processes. Some authors have extended thedefinition of DSS to include any system that might support decision making. Sprague (1980)defines DSS by its characteristics:
1. DSS tends to be aimed at the less well structured, underspecified problem that upperlevel managers typically face;
2. DSS attempts to combine the use of models or analytic techniques with traditional dataaccess and retrieval functions;
3. DSS specifically focuses on features which make them easy to use by noncomputer people in an interactive mode; and
4. DSS emphasizes flexibility and adaptability to accommodate changes inthe environment and the decision making approach of the user.
DSSs include knowledge-based systems. A properly designed DSS is an interactive software- based system intended to help decision makers compile useful information from a combinationof raw data, documents, and personal knowledge, or business models to identify and solve
problems and make decisions.
Typical information that a decision support application might gather and present includes:
inventories of information assets (including legacy and relational data sources, cubes, datawarehouses, and data marts) ,
comparative sales figures between one period and the next, projected revenue figures based on product sales assumptions.
Executive Information System (EIS)Definition - What does Ex ecutive I nf ormation System(EIS) mean?
An executive information system (EIS) is a decision support system (DSS) used to assist seniorexecutives in the decision-making process. It does this by providing easy access to importantdata needed to achieve strategic goals in an organization. An EIS normally features graphicaldisplays on an easy-to-use interface. Executive information systems can be used in manydifferent types of organizations to monitor enterprise performance as well as to identifyopportunities and problems.
UNIT IV
ACID Properties
ACID properties are an important concept for databases. The acronym stands for Atomicity,Consistency, Isolation, and Durability.
http://en.wikipedia.org/wiki/Decision_making_processhttp://en.wikipedia.org/wiki/Systemhttp://en.wikipedia.org/wiki/Decision_makinghttp://en.wikipedia.org/wiki/Problemhttp://en.wikipedia.org/wiki/Managementhttp://en.wikipedia.org/wiki/Data_accesshttp://en.wikipedia.org/wiki/Data_accesshttp://en.wikipedia.org/wiki/Flexibilityhttp://en.wikipedia.org/wiki/Adaptabilityhttp://en.wikipedia.org/wiki/Knowledge_environmenthttp://en.wikipedia.org/wiki/Decision_makinghttp://en.wikipedia.org/wiki/Expert_systemhttp://en.wikipedia.org/wiki/Data_warehousehttp://en.wikipedia.org/wiki/Data_warehousehttp://en.wikipedia.org/wiki/Data_marthttp://en.wikipedia.org/wiki/Data_marthttp://en.wikipedia.org/wiki/Data_warehousehttp://en.wikipedia.org/wiki/Data_warehousehttp://en.wikipedia.org/wiki/Expert_systemhttp://en.wikipedia.org/wiki/Decision_makinghttp://en.wikipedia.org/wiki/Knowledge_environmenthttp://en.wikipedia.org/wiki/Adaptabilityhttp://en.wikipedia.org/wiki/Flexibilityhttp://en.wikipedia.org/wiki/Data_accesshttp://en.wikipedia.org/wiki/Data_accesshttp://en.wikipedia.org/wiki/Managementhttp://en.wikipedia.org/wiki/Problemhttp://en.wikipedia.org/wiki/Decision_makinghttp://en.wikipedia.org/wiki/Systemhttp://en.wikipedia.org/wiki/Decision_making_process -
8/11/2019 Clientserver Notes
12/43
The ACID properties of a DBMS allow safe sharing of data. Without these ACID properties,everyday occurrences such using computer systems to buy products would be difficult and the
potential for inaccuracy would be huge. Imagine more than one person trying to buy the samesize and color of a sweater at the same time -- a regular occurrence. The ACID properties make it
possible for the merchant to keep these sweater purchasing transactions from overlapping eachother -- saving the merchant from erroneous inventory and account balances.
AtomicityThe atomicity property identifies that the transaction is atomic. An atomic transaction is eitherfully completed, or is not begun at all. Any updates that a transaction might affect on a systemare completed in their entirety. If for any reason an error occurs and the transaction is unable tocomplete all of its steps, the then system is returned to the state it was in before the transactionwas started. An example of an atomic transaction is an account transfer transaction. The moneyis removed from account A then placed into account B. If the system fails after removing themoney from account A, then the transaction processing system will put the money back intoaccount A, thus returning the system to its original state. This is known as a rollback , as we saidat the beginning of this chapter..ConsistencyA transaction enforces consistency in the system state by ensuring that at the end of anytransaction the system is in a valid state. If the transaction completes successfully, then allchanges to the system will have been properly made, and the system will be in a valid state. Ifany error occurs in a transaction, then any changes already made will be automatically rolled
back. This will return the system to its state before the transaction was started. Since the systemwas in a consistent state when the transaction was started, it will once again be in a consistent
state.Looking again at the account transfer system, the system is consistent if the total of all accountsis constant. If an error occurs and the money is removed from account A and not added toaccount B, then the total in all accounts would have changed. The system would no longer beconsistent. By rolling back the removal from account A, the total will again be what it should be,and the system back in a consistent state.IsolationWhen a transaction runs in isolation , it appears to be the only action that the system is carryingout at one time. If there are two transactions that are both performing the same function and arerunning at the same time, transaction isolation will ensure that each transaction thinks it hasexclusive use of the system. This is important in that as the transaction is being executed, thestate of the system may not be consistent. The transaction ensures that the system remainsconsistent after the transaction ends, but during an individual transaction, this may not be thecase. If a transaction was not running in isolation, it could access data from the system that maynot be consistent. By providing transaction isolation, this is prevented from happening.Durability
-
8/11/2019 Clientserver Notes
13/43
A transaction is durable in that once it has been successfully completed, all of the changes itmade to the system are permanent. There are safeguards that will prevent the loss of information,even in the case of system failure. By logging the steps that the transaction performs, the state ofthe system can be recreated even if the hardware itself has failed. The concept of durabilityallows the developer to know that a completed transaction is a permanent part of the system,regardless of what happens to the system later on.
Transaction ModelsThis topic describes the relationship between the transaction programming models and theinfrastructure components Microsoft provides.When using transactions in Windows Communication Foundation (WCF), it is important tounderstand that you are not selecting between different transactional models, but rather operatingat different layers of an integrated and consistent model.The following sections describe the three primary transaction components.Windows Communication Foundation TransactionsThe transaction support in WCF allows you write transactional services. In addition, with itssupport for the WS-AtomicTransaction (WS-AT) protocol, applications can flow transactions toWeb services built using either WCF or third-party technology.In a WCF service or application, WCF transaction features provide attributes and configurationfor declaratively specifying how and when the infrastructure should create, flow, andsynchronize transactions.System.Transactions TransactionsThe System.Transactions namespace provides both an explicit programming model based on
the Transaction class, as well as an implicit programming model usingtheTransactionScope class, in which the infrastructure automatically manages transactions.For more information about how to create a transactional application using these two models,see Writing a Transactional Application. In a WCF service or application, System.Transactions provides the programming model forcreating transactions within a client application and for explicitly interacting with a transaction,when required, within a service.MSDTC TransactionsThe Microsoft Distributed Transaction Coordinator (MSDTC) is a transaction manager that
provides support for distributed transactions.For more information, see the DTC Programmer's Reference. In a WCF service or application, MSDTC provides the infrastructure for the coordination oftransactions created within a client or service.
Definition - What does Transaction Processin g M onitor (TPM ) mean?
http://void%280%29/http://void%280%29/http://msdn.microsoft.com/en-us/library/system.transactions(v=vs.110).aspxhttp://msdn.microsoft.com/en-us/library/system.transactions.transaction(v=vs.110).aspxhttp://msdn.microsoft.com/en-us/library/system.transactions.transactionscope(v=vs.110).aspxhttp://go.microsoft.com/fwlink/?LinkId=94947http://msdn.microsoft.com/en-us/library/system.transactions(v=vs.110).aspxhttp://void%280%29/http://go.microsoft.com/fwlink/?LinkId=94948http://go.microsoft.com/fwlink/?LinkId=94948http://void%280%29/http://msdn.microsoft.com/en-us/library/system.transactions(v=vs.110).aspxhttp://go.microsoft.com/fwlink/?LinkId=94947http://msdn.microsoft.com/en-us/library/system.transactions.transactionscope(v=vs.110).aspxhttp://msdn.microsoft.com/en-us/library/system.transactions.transaction(v=vs.110).aspxhttp://msdn.microsoft.com/en-us/library/system.transactions(v=vs.110).aspxhttp://void%280%29/http://void%280%29/ -
8/11/2019 Clientserver Notes
14/43
A transaction processing monitor (TPM) is a program that monitors transactions from one stageto the next, ensuring that each one completes successfully; if not, or if an error occurs, the TMMonitor takes the appropriate action. A transaction processing monitors main purpose/objectiveis to allow resource sharing and assure optimal use of the resources by applications.
TPMs allow sharing of expensive database connections TPMs hides the interprocess communications details from programmers TPMs coordinate transaction processing TPMs check authorisation of processes
Examples of commonly used TPMonitors include:
CustomerInformationControlSystem, or CICS in short. Mostly found in IBM
environments TuxedoMonitor for the Unix environment ApplicationServers using the JavaTwoEnterpriseEdition for the Unix environment Encina for Unix (Is this in the same league as the other products?) MicrosoftTransactionServer, or MTS. Now superseded by ComPlus which is also used
in DotNet environments. IbmIms
The following Software Products are probably not classified as TransactionProcessingMonitor s?
ComPlus provides an environment and services to supporta TransactionProcessingMonitor, but should not be viewed asa TransactionProcessingMonitor, which is a software product. A closer match would
probably be the MTS component within a Windows 2000 Server. A WebServer such as InternetInformationServer (IIS). A closer match would be the IIS
server(s) running under the management services provided by a product such asMicrosoftApplicationCenter.
Sharing of resources
The first objective of a TransactionProcessingMonitor is to enable sharing of resources and theoptimum use of those resources by the application.
This point is quite a key point. For a longer explanation, just consider some application that runsa fat client on the client workstation and owns its dedicated link to the database. This kind of
http://c2.com/cgi/wiki?CustomerInformationControlSystemhttp://c2.com/cgi/wiki?TuxedoMonitorhttp://c2.com/cgi/wiki?ApplicationServerhttp://c2.com/cgi/wiki?JavaTwoEnterpriseEditionhttp://c2.com/cgi/wiki?MicrosoftTransactionServerhttp://c2.com/cgi/wiki?ComPlushttp://c2.com/cgi/wiki?DotNethttp://c2.com/cgi/wiki?IbmImshttp://c2.com/cgi/wiki?edit=TransactionProcessingMonitorshttp://c2.com/cgi/wiki?ComPlushttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?WebServerhttp://c2.com/cgi/wiki?InternetInformationServerhttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?InternetInformationServerhttp://c2.com/cgi/wiki?WebServerhttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?TransactionProcessingMonitorhttp://c2.com/cgi/wiki?ComPlushttp://c2.com/cgi/wiki?edit=TransactionProcessingMonitorshttp://c2.com/cgi/wiki?IbmImshttp://c2.com/cgi/wiki?DotNethttp://c2.com/cgi/wiki?ComPlushttp://c2.com/cgi/wiki?MicrosoftTransactionServerhttp://c2.com/cgi/wiki?JavaTwoEnterpriseEditionhttp://c2.com/cgi/wiki?ApplicationServerhttp://c2.com/cgi/wiki?TuxedoMonitorhttp://c2.com/cgi/wiki?CustomerInformationControlSystem -
8/11/2019 Clientserver Notes
15/43
application is generally referred to as a two tier application: one tier being the application and theother tier the database. In this kind of model:
You can run an application on a LAN with a limited number of users (up to severalhundreds),
You will need a big database machine with a lot of processes that are commonly doingnothing but wait for the user rollback buffers to commit,
You can have programmers that will forget to commit or rollback transactions and soorganize the possibility to lock for long periods of time some data in the database,
You cannot scale very properly because you will reach a limit where the databasemachine cannot accept more database connections while guaranteeing correct responsetimes.
The main idea of the TPM (on Unix-like platforms) is to introduce a layer of processes betweenthe client side application and the database. Each TPM process will own one databaseconnection. This process will be in charge of executing application code for a particulartransaction or set of transactions. That means that the "TPM process" is made of two parts : one
part being the monitor stack (TPM libraries) and the other being the application code linkedtogether by the application developer. The link can build a process with one or severaltransactions in it. Unix-like TPM ususally support programmingin CeeLanguage, CobolLanguage orCeePlusPlus.
The flow will be different in that model than in the two tier application model:
The client side application invokes a "service" with data marshaled in the appropriateformat; that means that the client application has some knowledge of:
o The TPM remote invocation language (probably a client middleware stackembedded into the client application),
o Or the knowledge of a "generic" way to call the TPM services through "standard" protocols (such as LU6.2, RPC, RMI/IIOP, proprietary formats, WSDL, etc.);
The TPM chooses (commonly some kind of intelligent TPM agent) what process willhandle the query (based on certain criteria such as addressing or load balancingconcerns);
The TPM processes unmarshals the message and calls back the application code;
The application code does its stuff in the database and possibly commit or rollback thetransaction;
The TPM process can commit or rollback the transaction as well (when the TPM isconfigured to handle the database resource manager, the TPM commits or rollbacks);
The answer is wrapped back in the appropriate format and sent back the the clientapplication.
http://c2.com/cgi/wiki?CeeLanguagehttp://c2.com/cgi/wiki?CobolLanguagehttp://c2.com/cgi/wiki?CeePlusPlushttp://c2.com/cgi/wiki?CeePlusPlushttp://c2.com/cgi/wiki?CobolLanguagehttp://c2.com/cgi/wiki?CeeLanguage -
8/11/2019 Clientserver Notes
16/43
Right after the answer, the same TPM process can:
Process another transaction (note that the TPM process is not suppose to "remember"something about the previous transaction - so the model is basically stateless);
Get a clean context for the application code to run again.
Other TPM services
There are several other potential services provided by the TPM:
Coordination of resource managers (typically a database engine, a transactional fileengine, a queue system, coordinated one by one or all together in XA standard, etc.);
Load-balancing and spawning of new TPM processes in case they are needed (dynamicworkload management, process restart in case of core dump),
Security access to services,
Routing services (very often, the notion of "domain" is used), Wrapping and unwrapping respectively data messages into messages and the messages
into data structures, Monitoring for operations, Protocol stack management, Quite often "Queue to queue" guaranteed delivery services, Error handling (such as process restart).
DEFINITION OF:GROUPWARE
Software that supports multiple users working on related tasks in local and remotenetworks. Also called "collaborative software," groupware is an evolving concept that ismore than just multiuser software which allows access to the same data. Groupware
provides a mechanism that helps users coordinate and keep track of ongoing projectstogether.
Lotus Notes is often considered the father of groupware, because it was the first to popularize a multifunction groupware system and development environment.
A fundamental component of groupware is e-mail, because e-mail is used to notify teammembers, obtain responses and send alerts. E-mail messages include live links todatabases, intranets and the Internet. Instant messaging (IM) is also widely used.Groupware Is Comprehensive Groupware also includes document sharing and document management, groupcalendaring and scheduling, group contact and task management, threaded discussions,text chat, data conferencing and audio and videoconferencing. Workflow, which allows
-
8/11/2019 Clientserver Notes
17/43
messages and documents to be routed to the appropriate users, is often part of agroupware system.From Simple to Complex The Internet/intranet explosion focused attention on groupware because of the ease withwhich HTML pages could be created and shared. However, as documents became widelydistributed throughout the enterprise, security and synchronization problems surfaced.Document management became a problem, and access control and replication becameissues. Thus, what started out as a simple way to electronically publish information,wound up becoming a complex enterprise-wide system.Se eworkflow, contextualcollaboration, collaborative browsing and wares.
Groupware and WorkflowGroupware focuses on the information being processed and enabling users to share it. Workflowemphasizes the process, which acts as a container for the information. Groupware is "information
http://www.pcmag.com/encyclopedia/term/54851/workflowhttp://www.pcmag.com/encyclopedia/term/40285/contextual-collaborationhttp://www.pcmag.com/encyclopedia/term/40285/contextual-collaborationhttp://www.pcmag.com/encyclopedia/term/39965/collaborative-browsinghttp://www.pcmag.com/encyclopedia/term/54210/wareshttp://www.pcmag.com/encyclopedia/term/54210/wareshttp://www.pcmag.com/encyclopedia/term/39965/collaborative-browsinghttp://www.pcmag.com/encyclopedia/term/40285/contextual-collaborationhttp://www.pcmag.com/encyclopedia/term/40285/contextual-collaborationhttp://www.pcmag.com/encyclopedia/term/54851/workflow -
8/11/2019 Clientserver Notes
18/43
-
8/11/2019 Clientserver Notes
19/43
Management Group, an industry consortium. CORBA is available for most major
operating systems
3. JINI (Genie, JINI is not initials a joke; JINI actually doesnt stand for
anything.) JINI is developed on top of Java. JINI was released by Sun in January,
1999.
What is CORBA?The Common Object Request Broker Architecture (CORBA) is a standard developed by theObject Management Group (OMG) to provide interoperability among distributed objects.CORBA is the world's leading middleware solution enabling the exchange of information,independent of hardware platforms, programming languages, and operating systems. CORBA isessentially a design specification for an Object Request Broker (ORB), where an ORB provides
the mechanism required for distributed objects to communicate with one another, whether locallyor on remote devices, written in different languages, or at different locations on a network.
The CORBA Interface Definition Language, or IDL, allows the development of language andlocation-independent interfaces to distributed objects. Using CORBA, application componentscan communicate with one another no matter where they are located, or who has designed them.CORBA provides the location transparency to be able to execute these applications.
CORBA is often described as a "software bus" because it is a software-based communicationsinterface through which objects are located and accessed. The illustration below identifies the
primary components seen within a CORBA implementation.
-
8/11/2019 Clientserver Notes
20/43
-
8/11/2019 Clientserver Notes
21/43
provides an overview of how the IDL is translated to the corresponding language (in thisexample, C++), mapped to the source code, compiled, and then linked with the ORB library,resulting in the client and server implementation.
The basic steps for CORBA development include:
Create the IDL to Define the Application Interfaces The IDL provides the operating system and programming language independent interfaces to allservices and components that are linked to the ORB. The IDL specifies a description of any
services a server component exposes to the client. The term "IDL Compiler" is often used, butthe IDL is actually translated into a programming language.
Translate the IDL An IDL translator typically generates two cooperative parts for the client and serverimplementation, stub code and skeleton code. The stub code generated for the interface classes isassociated with a client application and provides the user with a well-defined ApplicationProgramming Interface (API). In this example, the IDL is translated into C++.
Compile the Interface FilesOnce the IDL is translated into the appropriate language, C++ in this example, these interface
files are compiled and prepared for the object implementation.
Complete the ImplementationIf the implementation classes are incomplete, the spec and header files and complete bodies anddefinitions need to be modified before passing through to be compiled. The output is a completeclient/server implementation.
-
8/11/2019 Clientserver Notes
22/43
Compile the ImplementationOnce the implementation class is complete, the client interfaces are ready to be used in the clientapplication and can be immediately incorporated into the client process. This client process isresponsible for obtaining an object reference to a specific object, allowing the client to makerequests to that object in the form of a method call on its generated API.
Link the ApplicationOnce all the object code from steps three and five have been compiled, the objectimplementation classes need to be linked to the C++ linker. Once linked to the ORB library, inthis example, ORB express , two executable operations are created, one for the client and one forthe server.
Run the Client and ServerThe development process is now complete and the client will now communicate with the server.The server uses the object implementation classes allowing it to communicate with the objects
created by the client requests.In its simplest form, the server must perform the following:
Create the required objects. Notify the CORBA environment that it is ready to receive client requests. Process client requests by dispatching the appropriate servant.
CORBA Programming Definitions Within a CORBA development process, there are a number of unique terms specific to aCORBA implementation. Developers may find ou rGlossary of Terms helpful in understanding afull CORBA implementation.
Interoperability The first version of CORBA provided the IDL and standard mappings to just a few languages,and as the CORBA standard has matured, CORBA 2.0 added more language bindings(particularly C++ and Java) as well as General Inter-ORB Protocol (GIOP). When a client calls aCORBA operation, the client ORB sends a GIOP message to the server. The server ORBconverts this request into a call on the server object and then returns the results in a GIOP reply.This standard transfer syntax, specified by the Object Management Group, allows theinteroperability of ORB-to-ORB interaction and is designed to work over any transport protocol
meeting a minimal set of assumptions.
When GIOP is sent over TCP/IP, it is called Internet Inter ORB Protocol (IIOP). IIOP isdesigned to allow different ORB vendors to interoperate with one another. An example of thisinteroperability occurs when there is communication between an enterprise designed ORB, and asmaller real-time application, utilizing a real-time ORB.
Object Management Group (OMG)
http://www.ois.com/Products/glossary-of-terms.htmlhttp://www.omg.org/http://www.omg.org/http://www.omg.org/http://www.ois.com/Products/glossary-of-terms.html -
8/11/2019 Clientserver Notes
23/43
The OMG is a non-profit consortium created in 1989 to promote the theory and practice of object
technology for the development for distributed operating systems. The goal is to provide acommon architectural framework for object-oriented applications based on widely available
interface specifications. With a membership of over 800 members, representing large and smallcompanies within the computer industry, OMG leads the specification development efforts of
CORBA, OMG IDL, IIOP, OMA, UML, MOF, and CWM specifications.
The OMG does not produce software or implementation guidelines, only the specifications towhich OMG members respond to in Request For Information (RFI) and Requests for Proposals(RFP). By managing these specifications, the OMG supports the adoption process for themember companies interested in advancing the uses and applications of distributed object-oriented computing.
Object Management Architecture
The Object Management Architecture (OMA) embodies the OMG's vision for the componentsoftware environment. The architecture provides guidance on how standardization of componentinterfaces penetrate up - although not into - applications in order to create a plug-and-playcomponent software environment based on object technology.
Within the last several years, the OMG's work in modeling standards and the proliferation ofmiddleware technologies dictated an evolution of the OMA. An expanded vision of the OMAcan be found within the OMG's Model Driven Architecture (MDA) . The arrival of the MDA doesnot lessen the OMA's importance in OMG activity, however, as the OMG continues to requirethe guidance of the OMA in its advancement of the CORBA and related services specifications(see below.)
The OMA Reference Model shown above identifies and characterizes the components,interfaces, and protocols that compose the OMA. Central to the model - its communications heart- is the Object Request Broker (ORB) component that enables clients and objects tocommunicate in a distributed environment. The ORB provides an infrastructure allowing objectsto communicate independent of the specific platforms and techniques used to implement the
http://www.omg.org/mdahttp://www.omg.org/mdahttp://www.omg.org/mdahttp://www.omg.org/mda -
8/11/2019 Clientserver Notes
24/43
addressed objects. The ORB guarantees portability and interoperability of objects over a networkof heterogeneous systems. Specifications for the xe "Reference Model" ORB are containedin CORBA: Common Object Request Broker Architecture and Specification . It is worth notingthat over its life CORBA has been enhanced to support embedded and real-time systems as wellas those requiring fault tolerance and other Quality of Service requirements.
The CORBA Services component xe "Object Services;Object management architecture:ObjectServices" standardizes the life cycle management of objects. Functions are provided to createobjects, to control access to objects, to keep track of relocated objects and to consistentlymaintain the relationship between groups of objects. The CORBA Services components providethe generic environment in which single objects can perform their tasks. Standardization ofCORBA Services leads to consistency over different applications and improved productivity forthe developer. Specifications for the CORBA Services that have been adopted as standards bythe OMG are contained in CORBAservices: Common Object Services Specification.
Vertical CORBA Facilities represent components providing computing solutions for business problems within a specific vertical market (e.g., healthcare, manufacturing, finance). Listsof published and recently adopted Vertical CORBA Facility specifications are provided on theOMG web site. Horizontal CORBA Facilities represent those components providing supportacross an enterprise and across businesses. A Digital Asset Management component serves as anexample of such a component.
The Application Objects part xe "Object management architecture:ApplicationObject;Application Object" of the architecture represents those application objects performing
specific tasks for users. Whether not standardized or standardized (which typically representdomain frameworks) by the OMG, these interfaces provide access to application objects thatcan invoke methods on remote objects either statically or dynamically in a distributedenvironment through the ORB. An application is typically built from a large number of basicobject classes. New classes of application objects can be built by modification of existing classesthrough generalization or specialization of existing classes (inheritance) as provided by CORBAServices. The multi-object class approach to application development leads to improved
productivity for the developer and to options for end users to combine and configure theirapplications.
Compound DocumentsOLE compound documents enable users working within a single application to manipulate datawritten in various formats and derived from multiple sources. For example, a user might insertinto a word processing document a graph created in a second application and a sound objectcreated in a third application. Activating the graph causes the second application to load its userinterface, or at least that part containing tools necessary to edit the object. Activating the sound
ftp://ftp.omg.org/pub/docs/formal/99-10-07.pdfftp://ftp.omg.org/pub/docs/formal/99-10-07.pdfftp://ftp.omg.org/pub/docs/formal/99-10-07.pdfftp://ftp.omg.org/pub/docs/formal/98-12-09.pdfhttp://www.omg.org/technology/documents/specifications.htm#formalhttp://www.omg.org/technology/documents/specifications.htm#recenthttp://www.omg.org/technology/documents/specifications.htm#recenthttp://www.omg.org/technology/documents/specifications.htm#formalftp://ftp.omg.org/pub/docs/formal/98-12-09.pdfftp://ftp.omg.org/pub/docs/formal/99-10-07.pdf -
8/11/2019 Clientserver Notes
25/43
object causes the third application to play it. In both cases, a user is able to manipulate data fromexternal sources from within the context of a single document.OLE compound document technology rests on a foundation consisting of COM, structuredstorage, and uniform data transfer. As summarized below, each of these core technologies playsa critical role in OLE compound documents:COM
A compound document object is essentially a COM object that can be embedded in, orlinked to, an existing document. As a COM object, a compound document object exposesthe IUnknown interface, through which clients can obtain pointers to its other interfaces,including several, such as IOleObject , IOleLink , and IViewObject2 , that provide specialfeatures unique to compound document objects.
Structured Storage
A compound document object must implement the IPersistStorage or,
optionally, IPersistStream interfaces to manage its own storage. A container used tocreate compound documents must supply the IStorage interface, through which objectsstore and retrieve data. Containers almost always provide instances of IStorage obtainedfrom OLE's Compound Files implementation. Containers must also use anobject's IPersistStorage and/or IPersistStream interfaces.
Uniform Data Transfer
Applications that support compound documents must implement IDataObject becauseembedded objects and linked objects begin as data that has been transferred using specialOLE clipboard formats, rather than standard Microsoft Windows clipboard formats. In
other words, formatting data as an embedded or linked object is simply one more option provided by OLE's uniform data transfer model.
OLE's compound document technology benefits both software developers and users alike.Instead of feeling obligated to cram every conceivable feature into a single application, softwaredevelopers are now free, if they like, to develop smaller, more focused applications that rely onother applications to supply additional features. In cases where a software developer decides to
provide an application with capabilities beyond its core features, the developer can implementthese additional services as separate DLLs, which are loaded into memory only when theirservices are required. Users benefit from smaller, faster, more capable software that they can mixand match as needed, manipulating all required components from within a single masterdocument.
Dnt get framework of distributed objects
http://msdn.microsoft.com/en-us/library/windows/desktop/ms680509(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms680509(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms680509(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/dd542709(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/dd542709(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/dd542709(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms682297(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms682297(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms682297(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms691318(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms691318(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms679731(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms679731(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms679731(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms690091(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms690091(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms690091(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/aa380015(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/aa380015(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/aa380015(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms688421(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms688421(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms688421(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms688421(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/aa380015(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms690091(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms679731(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms691318(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms682297(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/dd542709(v=vs.85).aspxhttp://msdn.microsoft.com/en-us/library/windows/desktop/ms680509(v=vs.85).aspx -
8/11/2019 Clientserver Notes
26/43
Unit vURL:
Definition: URL is an acronym that stands for Uniform Resource Locator and is a reference (anaddress) to a resource on the Internet.
It's often easiest (though not entirely accurate) to think of a URL as the name of a file on thenetwork because most URLs refer to a file on some machine on the network. However, youshould remember that URLs can point to other resources on the network such as database queriesand command output.
The following is an example of a URL:
http://java.sun.com/This particular URL addresses the Java Web site hosted by Sun Microsystems. The URL shownabove, like all other URLs, has two main components separated by a colon (:):
the protocol identifier the resource name
In the example, http is the protocol identifier and //java.sun.com/ is the resource name.
The protocol identifier indicates the name of the protocol to be used to fetch the resource. Theexample uses the Hyper Text Transfer Protocol (HTTP), which is typically used to servehypertext documents. HTTP is just one of many different protocols used to access different typesof resources on the net. Other protocols include File Transfer Protocol (ftp), Gopher (gopher),File (file), and News (news).
The resource name is the complete address to the resource. The format of the resource namedepends entirely on the protocol used, but for many formats the resource name contains one ormore of the following components:
host name
the name of the machine the resource lives on
filename
the pathname to the file on the machine
http://java.sun.com/http://java.sun.com/ -
8/11/2019 Clientserver Notes
27/43
port number
the port number to connect to (this is typically optional)
reference
a reference to a named anchor within a resource; usually identifies a specific locationwithin a file (this is typically optional)
For many protocols, the host name and the filename are required and the port number andreference are optional. For example, the resource name for an HTTP URL must specify a serveron the network (host name) and the path to the document on that machine (filename), and canalso specify a port number and a reference. In the URL shown previously, java.sun.com is thehostname and the trailing slash '/' is short-hand for the file named /index.html.
When constructing any URL, put the protocol identifer first, followed by a colon (:), followed by
the resource name, like this:
protocolID :resourceName
The java.net package contains a class named URL that Java programs use to represent a URLaddress. Your Java program can construct a URL object, open a connection to it, and read to andwrite from it. The remaining pages of this lesson show you how to work with URL objects inyour Java programs.
HTML
What is HTML?
Hypertext Markup Language (HTML) is a syntax used to format a text document on the web.These documents are interpreted by web browsers such as Internet Explorer and Netscape
Navigator.
HTML can be created as standard ASCII text with "tags" included to pass on extra informationabout character formatting and page layout to a web browser. The fact that HTML is, in essence,ASCII text is what makes it so universally compatible. This fact also makes it easy to edit:almost all computers are equipped with a text editor that can be used to edit HTML.
-
8/11/2019 Clientserver Notes
28/43
How can I create an HTML page?
HTML pages can be created in a number of ways. An HTML page is essentially a text document.You can create one in the simplest of text editors such as Microsoft Notepad in Windows,SimpleText in Mac OS, or Pico in Unix. Using these tools, you will need to edit the HTML codeand insert HTML tags where necessary. You can also create pages using WYSIWYG (What YouSee Is What You Get) editors which do most of the work of coding for you. With WYSIWYGeditors, such as Macromedia Dreamweaver and Adobe GoLive, you can type in a page as youwould in a word processor, and the software adds formatting tags where necessary. You can thenlook into the code for fine-tuning.
Note: There are some WYSIWYG editors that do not create good HTML code. For instance,Microsoft FrontPage and particularly Microsoft Word will add extra tags that can make anHTML document quite large. Larger documents take longer to download. While you may notnotice this much while on campus at NIH, modem users at home can be inconvenienced by longwaits.
To save a file as HTML, open the text you wish to edit or type it into Notepad, and choose"File...Save As..." from the menu bar. Under "File name" give your file a name and change itsextension from ".txt" to ".html." Under "Save as type" switch to "All Files" then click "OK."
Notepad will save your file as ASCII text, and the ".html" or ".htm" extension will allow your browser to recognize it as an HTML file. (Hint - When naming an HTML file, it is a good idea touse a name without any spaces or uppercase letters. So, if you wanted to name a file Test page,some options would be testpage or test_page.)
To open your file in Netscape, choose "File...Open Page..." from Netscape's menu bar, andclick "Choose File." Navigate to the drive and directory in which you saved your HTML, anddouble click on the file.
To edit your HTML, go back to Notepad, make your changes, and choose "File...Save" fromthe menu bar. Then go back to Netscape, and click the "Reload" button to bring in your latestchanges.
What are Tags?
Tags are what we use to structure an HTML page. Tags start with a ''. For example, the center tag is ''. To stop centering something, we need anending, or closing tag. Closing tags look exactly like opening tags, except after the first '
-
8/11/2019 Clientserver Notes
29/43
HTML Structure
An HTML document has a definite structure that must be specified to the browser. The HTML's beginning and end must be defined, as well as the document's HEAD (which containsinformation for the browser that does not appear in the browser's main window) and its BODY(which contains the text that will appear in the browser's main window). The use and order oftags that define the HTML structure are described below.
Marks the beginning of your HTML
Begins the heading section of an HTML document
... Gives an HTML document a title that appears on the browser menu bar,also will appear on search engines or bookmarks referencing your site(must appear between the ... tags; should be straighttext, no tags
Defines the end of the heading
Defines the body of an HTML document (text contained within the tags appears in the main browser window). Can
be used with "BGCOLOR", "TEXT", "LINK", and "VLINK" attributes
Defines the end of your HTML document
Character Formatting and Page Layout
The following tags are used for character formatting (bold, italicized or underlined text, forinstance) and page layout (where and in what context that text appears on the page). These tagsare used in the body of an HTML document only.
Comment. This is a note for you. It will not be visible on the web page.
... Heading tag. through are valid. Can be used with the
"ALIGN" attribute.
...
Sets a paragraph apart from other text. Adds a line break after. isoptional. Can be used with the "ALIGN" attribute.
Line break (new line). Can be used with the "CLEAR" attribute. -
8/11/2019 Clientserver Notes
30/43
Horizontal rule. Can be used with "SIZE", "WIDTH" and "NOSHADE"attributes.
... Defines the beginning and end of an ordered list (numbered).
... Unordered list (bulleted).
List Item. Must appear before each item in any of the above lists to set itapart from other items.
... Centers any item or group of items
... Emphasized text (usually italic).
... Strong emphasis (usually bold).
... A sample of code (usually courier font).
... Changes the appearance of the text in your page. Can be used with"SIZE", "COLOR" and "FACE" attributes.
... Creates Table. Can be used with "BORDER", "ALIGN", and "WIDTH"attributes.
... Table row
... Table header. Can be used with "ALIGN", "VALIGN", "COLSPAN","ROWSPAN", and "WIDTH" attributes.
... Table data. Can be used with "ALIGN", "VALIGN", "COLSPAN","ROWSPAN", and "WIDTH" attributes.
-
8/11/2019 Clientserver Notes
31/43
Links
... Creates a hypertext link to another page.
... Creates a link to an anchor in another web page.
... Creates an anchor within a document that can be linked to.
Inserts a graphic into the web page. "SRC" is a required attribute. "HEIGHT", "WIDTH","ALT", "BORDER" and "ALIGN" are optional attributes.
Character Entities (escape sequences)
Some characters that have special uses or meanings for browsers may not always appear as youintend in your browser. To get a browser to display a character without applying that character'sspecial use, "escape sequences" are used. Below are a few frequently used sequences.
Character Numeric Entity Character Entity Description
" " " Double Quotation Mark
# # Number Sign
% % & Ampersand
< < < Less Than
> > > Greater Than
Blank Space
Http
-
8/11/2019 Clientserver Notes
32/43
-
8/11/2019 Clientserver Notes
33/43
esx-server IP address or a DNS name.
/host List of configuration files that you can access. (Use /host to retrieve the list.)
/host/file A specific ESX/ESXi configuration file.
HTTP Host Access (/host URL) shows ESX host configuration files and the correspondingHTTP/HTTPS methods for access. The set of files might change from version to version.
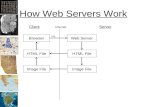
Three-tiered client/server architectureA common design of client/server systems uses three tiers:
1. A client that interacts with the user2. An application server that contains the business logic of the application3. A resource manager that stores data
This principle is shown in Figure 1. Figure 1. Three-tiered client/server architecture
Three-Ti er Cli ent/Server
A three-tier client/server adds an additional layer/tier to the client/server-based two-tier models.This additional layer is a server tier that acts as an intermediary or middleware appliance. In atypical implementation scenario, the client or first tier holds the application
presentation/interface and broadcasts all of its application-specific requests to the middlewaretier server. The middleware or second tier calls the application logic server or third tier for
https://pubs.vmware.com/vsphere-50/topic/com.vmware.wssdk.pg.doc_50/PG_ChC_Http_Access.21.3.html#1070296http://publib.boulder.ibm.com/infocenter/txformp/v6r1/topic/com.ibm.cics.tx.doc/erziaz/erziaz0105.html#erziaz01-gen4__threetieredfighttp://publib.boulder.ibm.com/infocenter/txformp/v6r1/topic/com.ibm.cics.tx.doc/erziaz/erziaz0105.html#erziaz01-gen4__threetieredfighttps://pubs.vmware.com/vsphere-50/topic/com.vmware.wssdk.pg.doc_50/PG_ChC_Http_Access.21.3.html#1070296 -
8/11/2019 Clientserver Notes
34/43
application logic. The distribution of the entire application logic across three tiers helps optimizethe overall application access and layer/tier level development and management.
HTML Forms
HTML forms are used to pass data to a server.
An HTML form can contain input elements like text fields, checkboxes, radio-buttons, submit buttons and more. A form can also contain select lists, textarea, fieldset, legend, and labelelements.
The tag is used to create an HTML form:
.
input elements .
HTML Forms - The Input Element
The most important form element is the element.
The element is used to select user information.
An element can vary in many ways, depending on the type attribute. An element can be of type text field, checkbox, password, radio button, submit button, and more.
The most common input types are described below.
Text Fields
defines a one-line input field that a user can enter text into:
First name:
Last name: -
8/11/2019 Clientserver Notes
35/43
How the HTML code above looks in a browser:
First name:
Last name:
Note: The form itself is not visible. Also note that the default width of a text field is 20characters.
Password Field
defines a password field:
Password:
How the HTML code above looks in a browser:
Password:
Note: The characters in a password field are masked (shown as asterisks or circles).
Radio Buttons
defines a radio button. Radio buttons let a user select ONLY ONE of alimited number of choices:
Male
FemaleHow the HTML code above looks in a browser:
Male
Female
-
8/11/2019 Clientserver Notes
36/43
Checkboxes
defines a checkbox. Checkboxes let a user select ZERO or MORE
options of a limited number of choices.
I have a bike
I have a carHow the HTML code above looks in a browser:
I have a bike
I have a car
Submit Button
defines a submit button.
A submit button is used to send form data to a server. The data is sent to the page specified in theform's action attribute. The file defined in the action attribute usually does something with the
received input:
Username:
How the HTML code above looks in a browser:
Username:Submit
If you type some characters in the text field above, and click the "Submit" button, the browserwill send your input to a page called "demo_form_action.asp". The page will show you thereceived input.
-
8/11/2019 Clientserver Notes
37/43
-
8/11/2019 Clientserver Notes
38/43
Send e-mail from a formHow to send e-mail from a form.
HTML Form Tags
= Tag added in HTML5.
Tag Description
Defines an HTML form for user input
Defines an input control
Defines a multiline input control (text area)
Defines a label for an element
Groups related elements in a form
Defines a caption for a element
Defines a drop-down list
Defines a group of related options in a drop-down list
Defines an option in a drop-down list
Defines a clickable button
Specifies a list of pre-defined options for input controls
Defines a key-pair generator field (for forms)
Defines the result of a calculation
http://www.w3schools.com/html/tryit.asp?filename=tryhtml_form_mailhttp://www.w3schools.com/tags/tag_form.asphttp://www.w3schools.com/tags/tag_form.asphttp://www.w3schools.com/tags/tag_input.asphttp://www.w3schools.com/tags/tag_textarea.asphttp://www.w3schools.com/tags/tag_textarea.asphttp://www.w3schools.com/tags/tag_label.asphttp://www.w3schools.com/tags/tag_label.asphttp://www.w3schools.com/tags/tag_fieldset.asphttp://www.w3schools.com/tags/tag_fieldset.asphttp://www.w3schools.com/tags/tag_legend.asphttp://www.w3schools.com/tags/tag_legend.asphttp://www.w3schools.com/tags/tag_select.asphttp://www.w3schools.com/tags/tag_select.asphttp://www.w3schools.com/tags/tag_optgroup.asphttp://www.w3schools.com/tags/tag_optgroup.asphttp://www.w3schools.com/tags/tag_option.asphttp://www.w3schools.com/tags/tag_button.asphttp://www.w3schools.com/tags/tag_datalist.asphttp://www.w3schools.com/tags/tag_datalist.asphttp://www.w3schools.com/tags/tag_keygen.asphttp://www.w3schools.com/tags/tag_keygen.asphttp://www.w3schools.com/tags/tag_output.asphttp://www.w3schools.com/tags/tag_output.asphttp://www.w3schools.com/tags/tag_keygen.asphttp://www.w3schools.com/tags/tag_datalist.asphttp://www.w3schools.com/tags/tag_button.asphttp://www.w3schools.com/tags/tag_option.asphttp://www.w3schools.com/tags/tag_optgroup.asphttp://www.w3schools.com/tags/tag_select.asphttp://www.w3schools.com/tags/tag_legend.asphttp://www.w3schools.com/tags/tag_fieldset.asphttp://www.w3schools.com/tags/tag_label.asphttp://www.w3schools.com/tags/tag_textarea.asphttp://www.w3schools.com/tags/tag_input.asphttp://www.w3schools.com/tags/tag_form.asphttp://www.w3schools.com/html/tryit.asp?filename=tryhtml_form_mail -
8/11/2019 Clientserver Notes
39/43
As you traverse the vast frontier of the World Wide Web, you will come across documents thatmake you wonder, "How did they do this?" These documents could consist of, among otherthings, forms that ask for feedback or registration information, imagemaps that allow you to click
on various parts of the image, counters that display the number of users that accessed thedocument, and utilities that allow you to search databases for particular information. In mostcases, you'll find that these effects were achieved using the Common Gateway Interface,commonly known as CGI.
One of the Internet's worst-kept secrets is that CGI is astoundingly simple. That is, it's trivial indesign, and anyone with an iota of programming experience can write rudimentary scripts thatwork. It's only when your needs are more demanding that you have to master the more complexworkings of the Web. In a way, CGI is easy the same way cooking is easy: anyone can toast amuffin or poach an egg. It's only when you want a Hollandaise sauce that things start to get
complicated.
CGI is the part of the Web server that can communicate with other programs running on theserver. With CGI, the Web server can call up a program, while passing user-specific data to the
program (such as what host the user is connecting from, or input the user has supplied usingHTML form syntax). The program then processes that data and the server passes the program'sresponse back to the Web browser.
CGI isn't magic; it's just programming with some special types of input and a few strict rules on program output. Everything in between is just programming. Of course, there are special
techniques that are particular to CGI, and that's what this book is mostly about. But underlying itall is the simple model shown in Figure 1.1.
http://oreilly.com/openbook/cgi/ch01_01.html#CGI-CHP-1-FIG-1http://oreilly.com/openbook/cgi/ch01_01.html#CGI-CHP-1-FIG-1 -
8/11/2019 Clientserver Notes
40/43
F igur e 1.1: Simple diagram of CGI
Proxy-free threat protection from the world's largest threat detection network.
Websense Web Security blocks web threats to reduce malware infections, decrease help deskincidents and free up valuable IT resources. It has more than 100 security and filteringcategories, hundreds of web application and protocol controls, and 60-plus reports withcustomization and role-based access. You can easily upgrade to Web Security Gateway whendesired to get social media controls, SSL inspection, data loss prevention (DLP) and inline, real-time security from Websense ACE (Advanced Classification Engine). Top Featur es
Real-time security updates from the Websense ThreatSeeker Intelligence Cloud helpdefend against advanced malware, blended threats and spam.
Video controls protect network resources, provide custom allow/deny filters, enableYouTube educational videos, and provide control over viral, entertainment and surveillancevideos.
Network port monitoring with application and protocol controls provides control forhundreds applications and protocols.
Robust reporting includes more than 60 pre-defined reports that can be easily customized.Additional F eatures
Feature Description
Web Security andFiltering
Over 100 categories including security, productivity and bandwidth with real-time security updates from the WebsenseThreatSeeker Intelligence Cloud.
Remote UserAn optional remote filter agent provides web access to remoteusers for protection against threats and enforcement of
http://www.websense.com/content/websense-url-categories.aspxhttp://www.websense.com/content/websense-url-categories.aspxhttp://www.websense.com/content/web-security-gateway-features.aspxhttp://www.websense.com/content/websense-advanced-classification-engine.aspxhttp://www.websense.com/content/websense-threatseeker-network.aspxhttp://www.websense.com/content/websense-url-categories.aspxhttp://www.websense.com/content/ThreatSeeker.aspxhttp://www.websense.com/content/ThreatSeeker.aspxhttp://www.websense.com/content/ThreatSeeker.aspxhttp://www.websense.com/content/ThreatSeeker.aspxhttp://www.websense.com/content/websense-url-categories.aspxhttp://www.websense.com/content/websense-threatseeker-network.aspxhttp://www.websense.com/content/websense-advanced-classification-engine.aspxhttp://www.websense.com/content/web-security-gateway-features.aspxhttp://www.websense.com/content/websense-url-categories.aspxhttp://www.websense.com/content/websense-url-categories.aspx -
8/11/2019 Clientserver Notes
41/43
-
8/11/2019 Clientserver Notes
42/43
Intranet
Intranet is system in which multiple PCs are connected to each other.
PCs in intranet are not available to the world outside the intranet.
Usually each company or organization has their own Intranet network andmembers/employees of that company can access the computers in their intranet.
Each computer in Intranet is also identified by an IP Address which is unique among thecomputers in that Intranet.
Similarities in Internet and Intranet Intranet uses the internet protocols such as TCP/IP and FTP.
-
8/11/2019 Clientserver Notes
43/43
Intranet sites are accessible via web browser in similar way as websites in internet. Butonly members of Intranet network can access intranet hosted sites.
In Intranet, own instant messengers can be used as similar to yahoo messenger/ gtalkover the internet.
Differences in Internet and Intranet Internet is general to PCs all over the world whereas Intranet is specific to few PCs.
Internet has wider access and provides a better access to websites to large populationwhereas Intranet is restricted.
Internet is not as safe as Intranet as Intranet can be safely privatized as per the need.






![tcpdump : network traffic capture - Santa Monica Collegehomepage.smc.edu/morgan_david/linux/n-prog-01-tcpdump.pdf · tcpdump : network traffic capture David Morgan ... [root@rh clientserver]#](https://static.fdocuments.in/doc/165x107/5a7a499b7f8b9a27638bf648/tcpdump-network-traffic-capture-santa-monica-network-traffic-capture-david.jpg)